Synology SRM Safe Access & Firewall - how to block torrent content using Synology router?

Table of Contents
: Intro
: Synology router lineup
: How to block specific sites and torrent traffic?
- :: Safe Access - overview and profile creation
- :: Safe Access - web filter
- :: Firewall
- :: Firewall rules configuration
- :: Real-time traffic overview
- :: Special configuration for Chrome & Edge browsers
: Intro
As much as the Internet has contributed to the quality of life, the development of industry, business, and mutual relations in the last 30+ years, it has certainly (if not more) revealed its negative sides.
Theft and distribution of protected material, viruses, ransomware, malware, and other malicious software are at an absolute peak. Being disconnected from the Internet today is almost impossible both from the private and business side. Every aspect of our life depends to some extent on a quality connection with necessary services.
If we look a step further, the protection of children and young people is probably one of the tasks that the previous generation of parents did not have to face. Although there will always be a way to get to some prohibited content, protecting the home or business network, and therefore the computer and users, is something that is necessary today. Not so much for the purpose of banning and availability of certain material, but also because of the previously listed threats that mostly accompany such content.
The following will explain and show how Synology with its line of routers can help in scenarios that are very common today. Specifically, this article will focus on the two main elements of SRM (Synology Router Manager), Safe Access, and Firewall.
: Synology router lineup
Synology currently offers four routers. Two from the older Wi-fi 5 generation, and two new ones (this year's models) that support Wi-fi 6. It is not so important which router will be used because they all support all the options explained below since they come with the new SRM 1.3 operating system.

If you wish, you can view two separate reviews for the RT6600ax flagship model as well as the recently released WRX560 router at the available links below.


In the mentioned articles, there is also a section of the SRM operating system with some of its important features. In the following, we will deal with a specific scenario, so the emphasis will be on some elements that are not explained in the mentioned reviews.
: How to block specific sites and torrent traffic?
So how do you block content on the Internet, specifically torrent sites, while not being able to use any torrent applications even if someone gets hold of the torrent file or magnet link in some other way?
This is a frequent question, especially in a corporate environment, where configuring and maintaining such scenarios is much easier by using enterprise network equipment and methods.
For the SOHO (small office, home office) segment, such equipment is certainly not, if nothing else, profitable, so the question arises as to how to solve this in the simplest way with the network device you have. If we look at ISP routers, this can't be done for the reason that some of them will not even have such capabilities, and those that do may block that particular configuration from the user.
Just to be clear. Blocking torrent traffic is not a one-button solution by any means, nor is it easy to achieve unless you go with very rigorous and precise settings that need to be maintained and monitored.
It is for this reason that the use of routers and other equipment that has mechanisms for blocking and controlling network traffic is necessary in order to ensure the quality and safety of all users and equipment.
:: Safe Access - overview and profile creation
The first step will certainly be to create a profile within the Safe Access application. SA comes installed with the SRM operating system and is one of the main icons on the desktop.
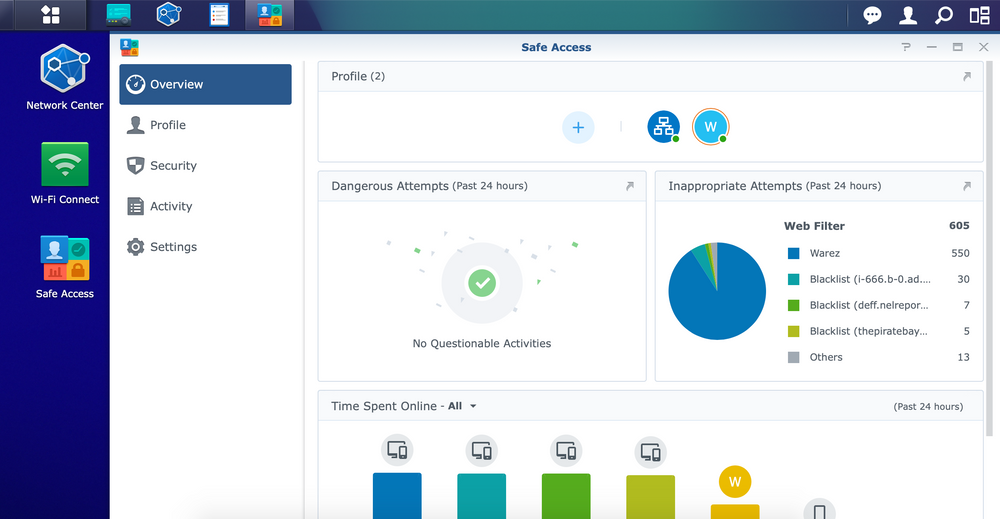
By starting the Safe Access application, we will be given the opportunity to create new user/device profiles or profiles that affect a specific configured network. Since SRM offers the creation of more than one network and VLAN support, we can also apply profiles to a specific network.
Regardless of what we choose, all settings and configurations are equally available in both cases.
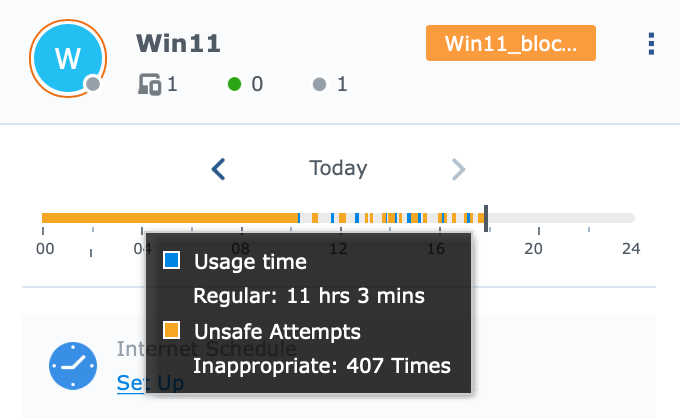
As you can see from the images, Safe Access will display all available profiles as well as quick statistics of any inappropriate attempts and their times.
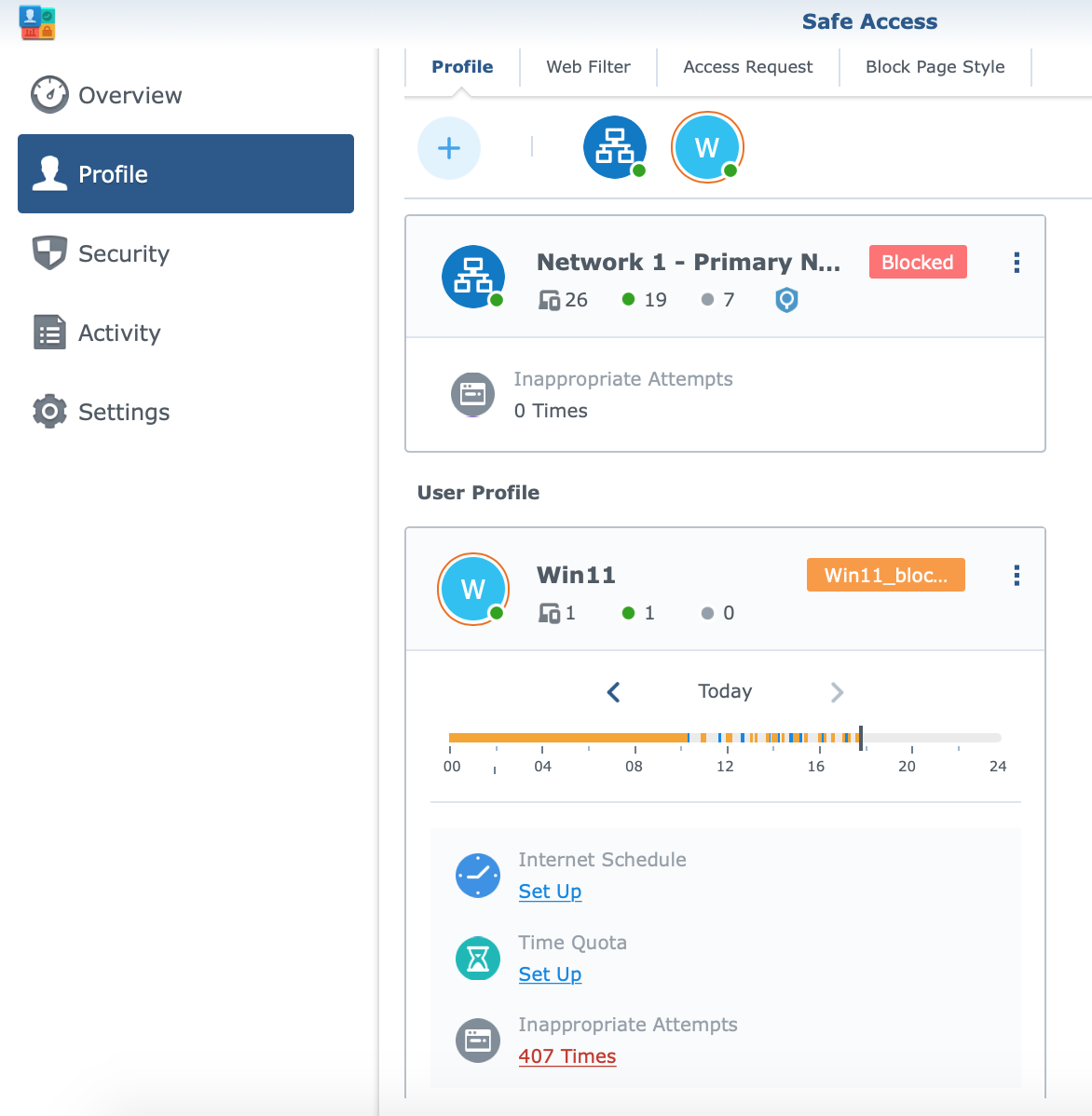
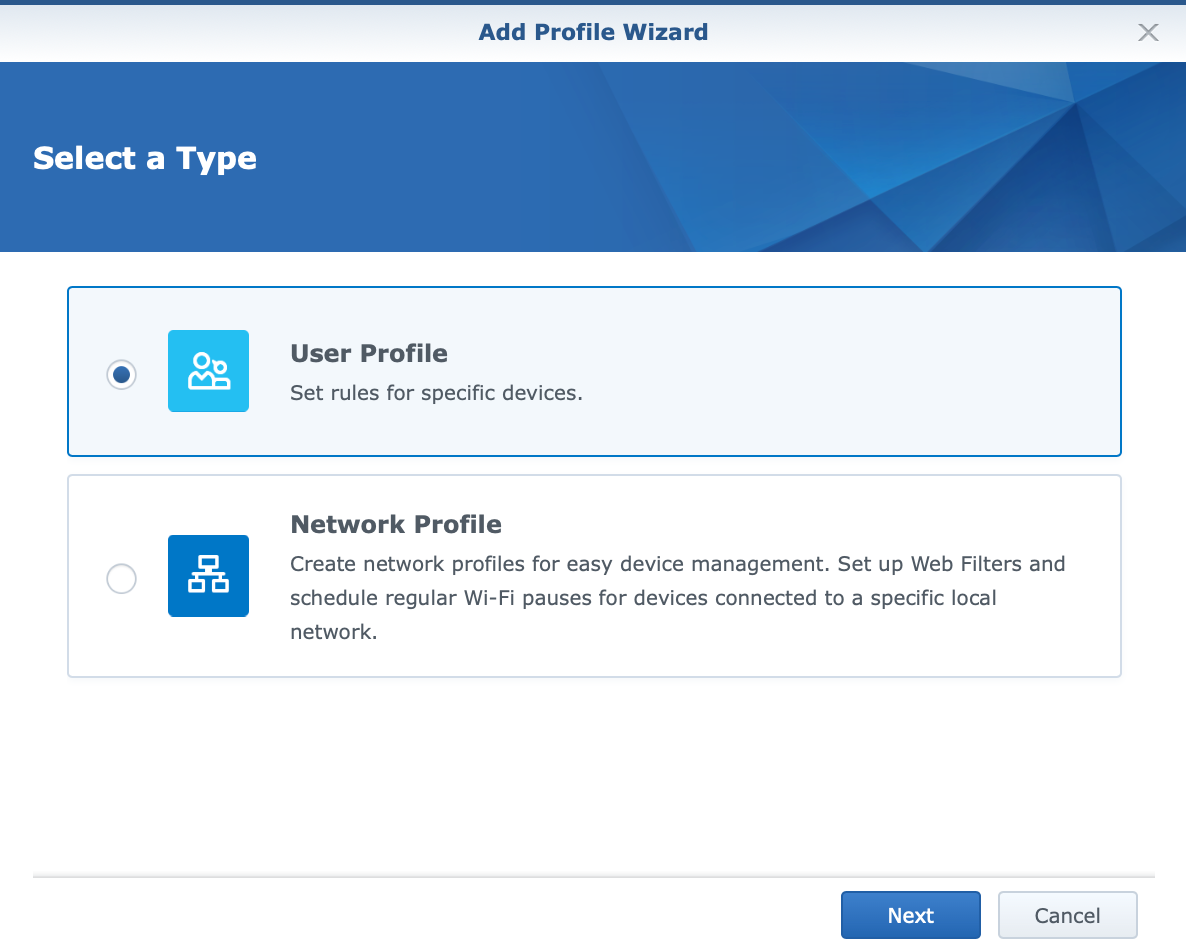
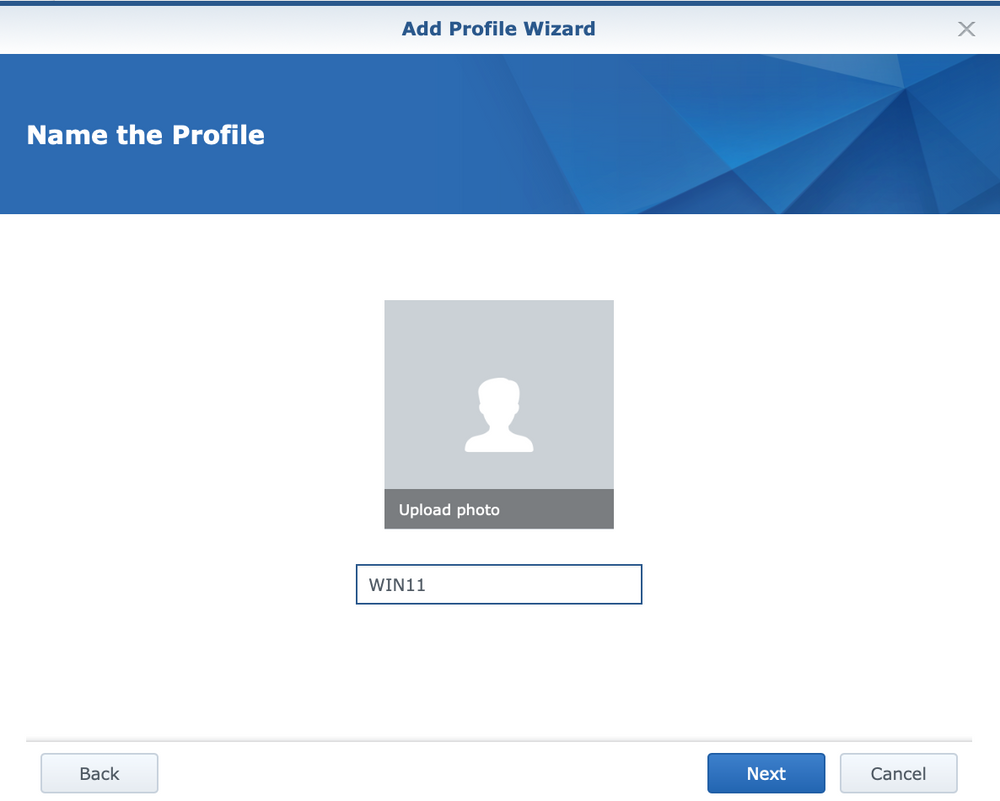
Following next will be an example on how to create a profile that will effectively block torrent traffic and access to associated sites. The creation of a profile begins with the Safe Access wizard, in which a specific device (or several devices) is associated to the specified policy.
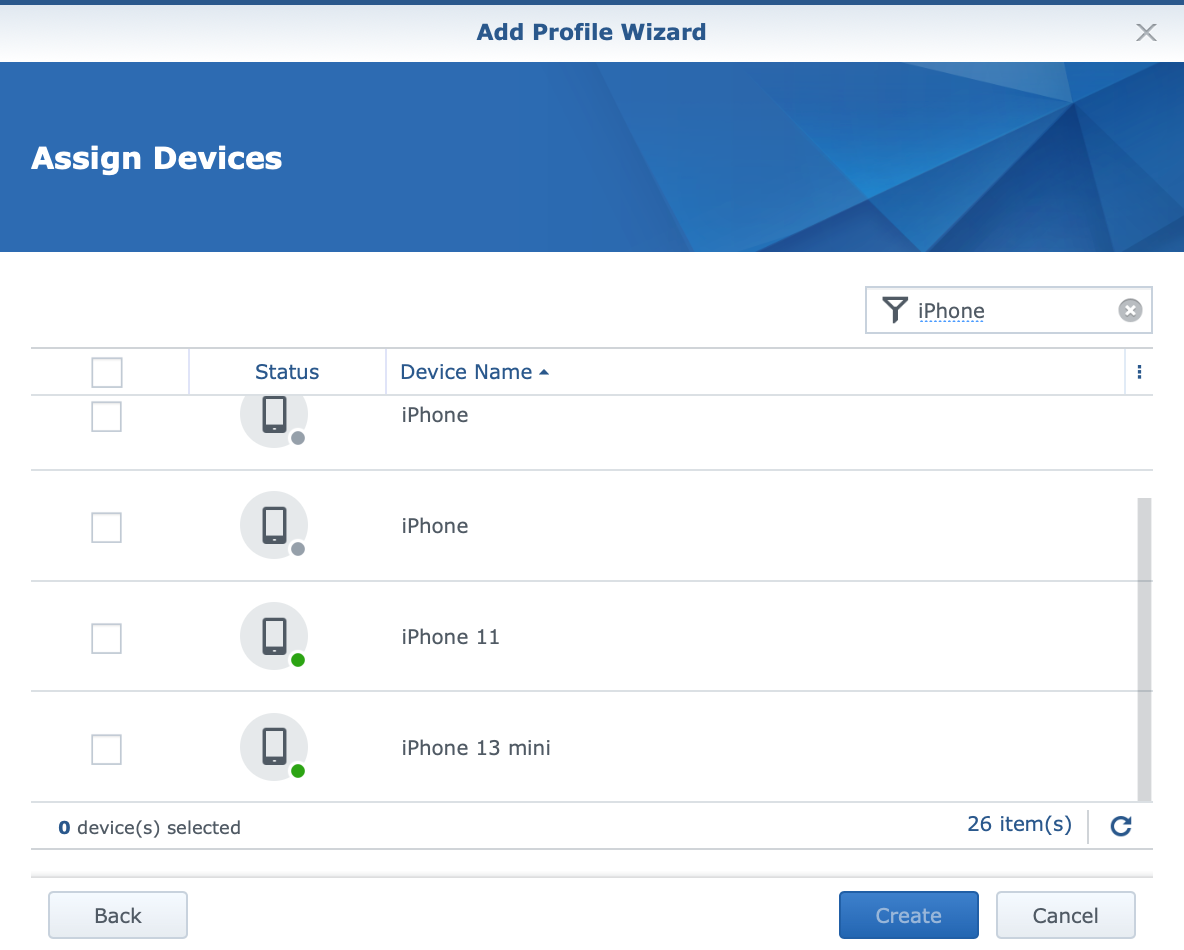
Now it's time to configure the web filter that will be associated with the profile, each of which will have a set of rules that will apply to all machines defined through that same profile.
Of course, if a computer or device was added incorrectly or was not added by mistake, changing the profile will enable subsequent corrections.
:: Safe Access - web filter
Safe Access has a number of pre-defined web filters ready for use, but if we wish, it is possible to define our own in order to more precisely determine the rules for accessing the content, as well as defining special black and white lists of allowed or blocked Internet destinations.
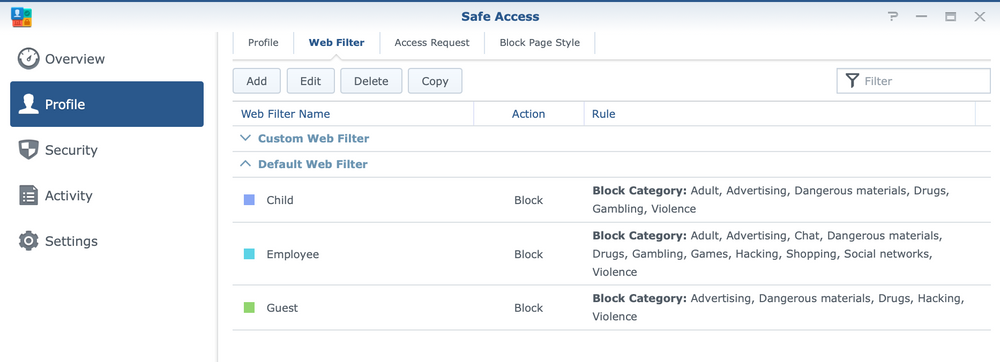
Profiles can be modified, deleted and cloned to become a template for a new profile.
Creating a new profile is also done through a wizard in several steps.
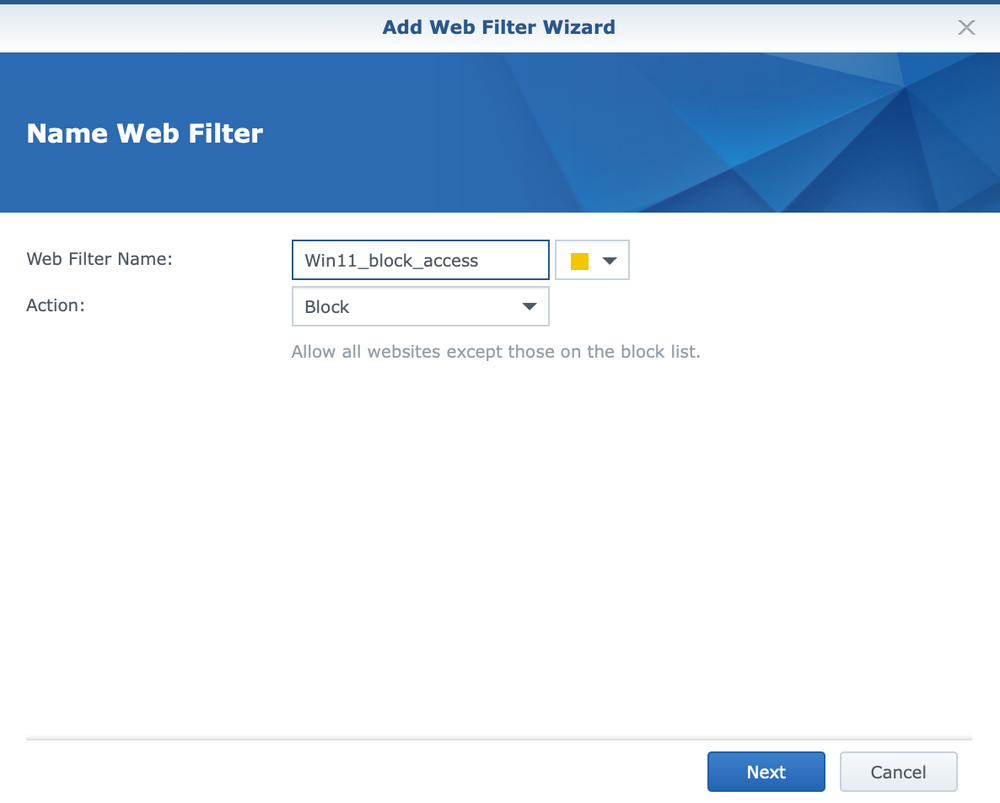
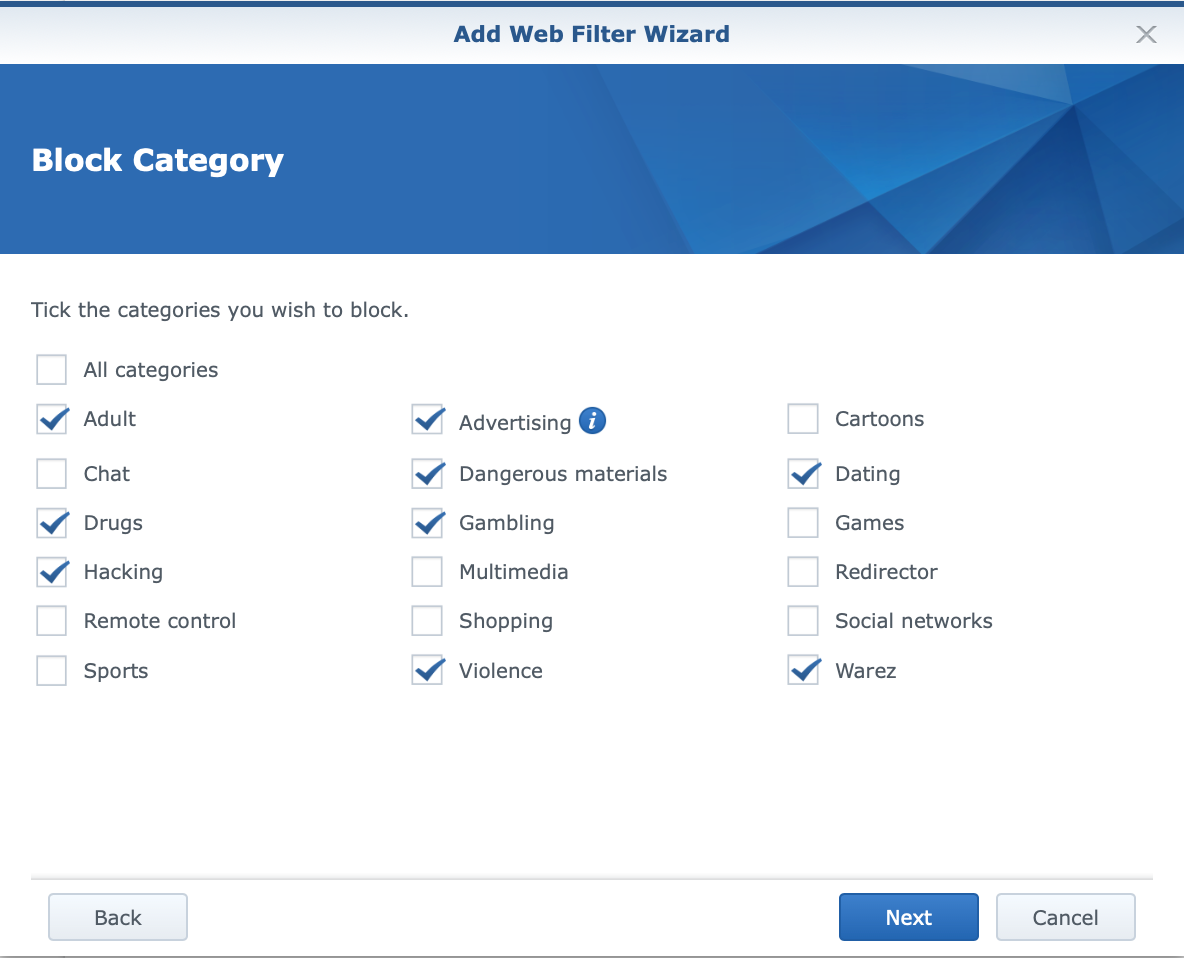
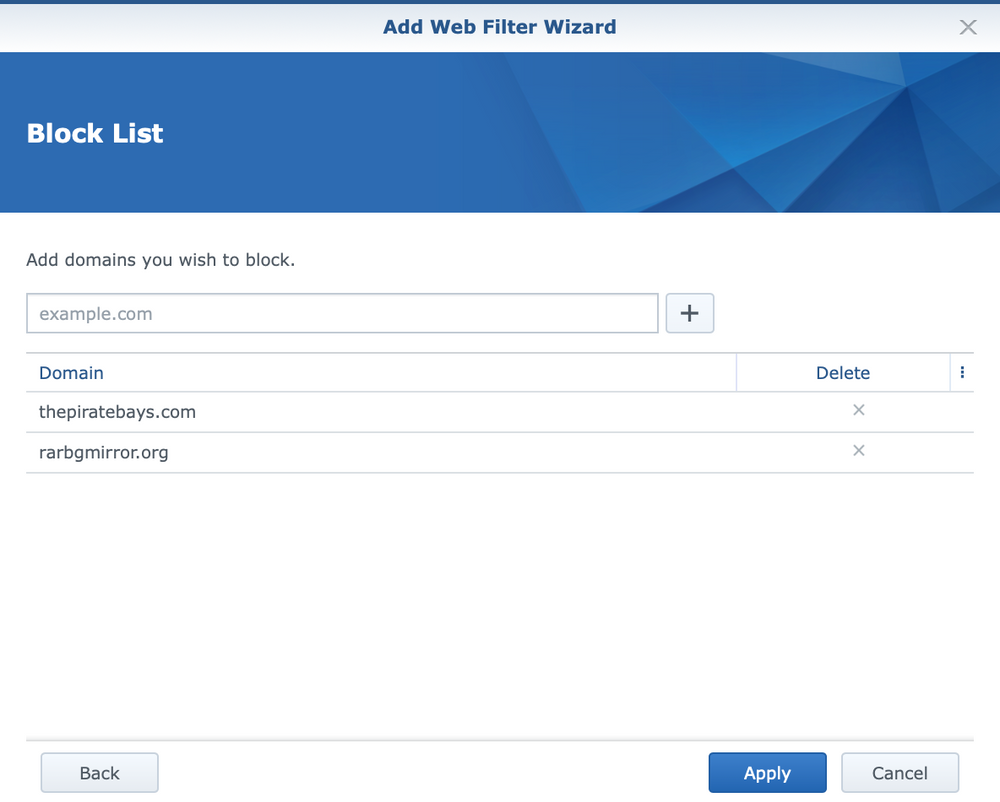
In addition to the primary name and action (blocking and access permission), within the filter it is possible to select previously defined categories to which we want to allow or deny access (depending on the selection in the first step of the wizard). Finally, we can additionally define specific domains to which we explicitly want to prohibit/allow access.
After the filter is assembled, the last thing that needs to be done is to attach it to the initially created profile. For this, it is necessary to open it and configure which filter we want to add on the web filter tab.
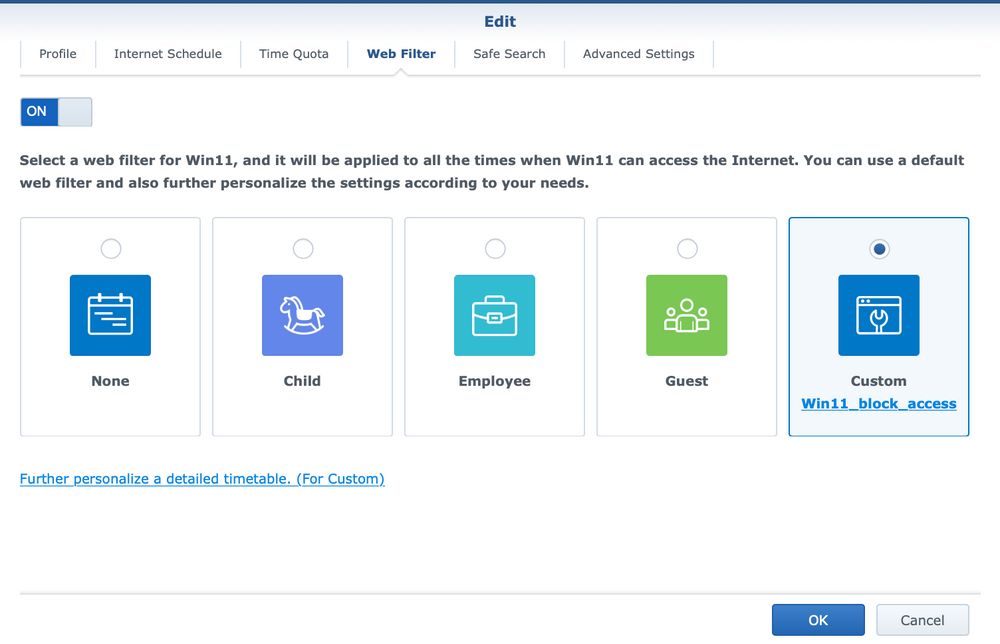
It should be noted that other parameters can be defined within the profile in addition to the specified filter, but this is currently not necessary as part of this specific scenario.
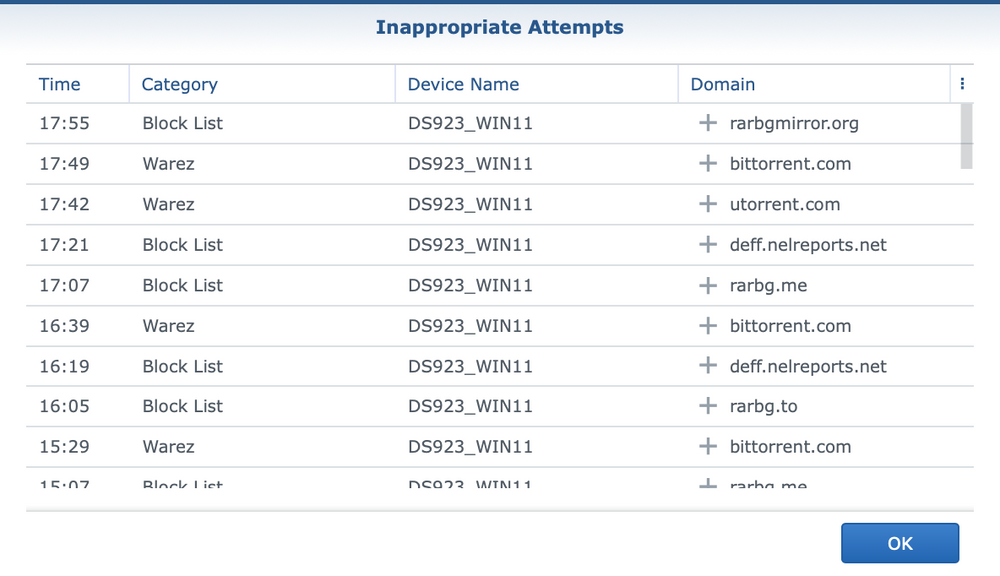
After the defined profile and the applied filter, access from the device to the prohibited destination will look like in the image.
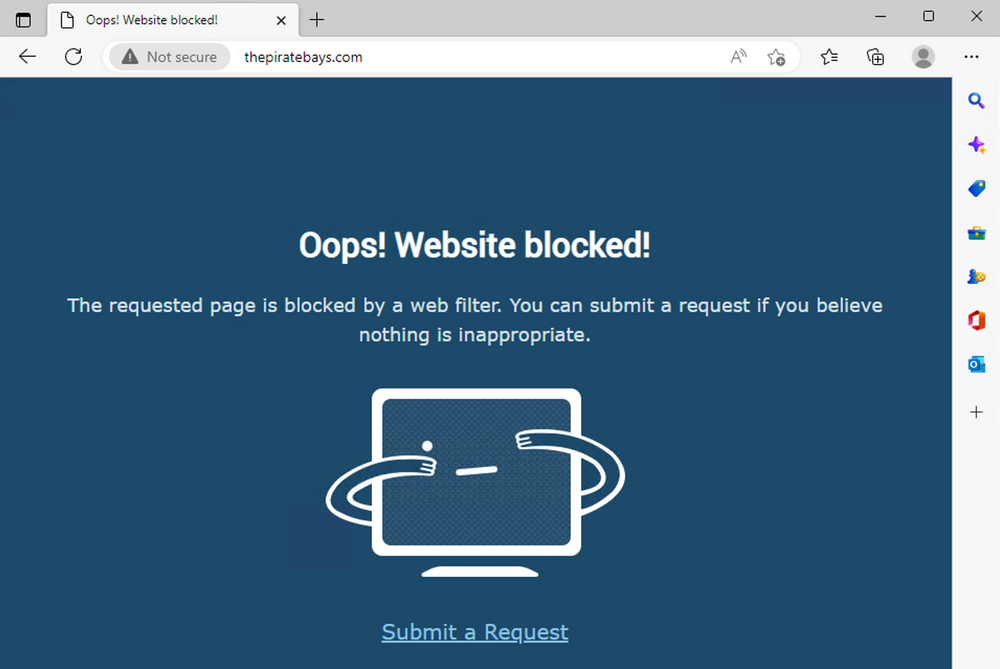
This is only one part of the story about blocking access to sites with unwanted content such as torrents (and precisely defined sites), but this will not prevent the torrent file or magnet link from being downloaded via some other method (say via chat or email) and then placed into a torrent client.
To block torrents from the perspective of protocols and ports, that's a separate story and Safe Access can't help with that. But blocking torrents is also not that easy. Lately, clients have become more powerful and flexible to allow end user access using dynamic ports every time they launch, so this creates a problem when blocking them.
The only way to do it well on the Synology router is through the firewall function.
:: Firewall
The important thing to know when configuring the SRM firewall is that the rules defined within it are respected from top to bottom, i.e. the waterfall principle. This means that the first rule that meets the criteria (either allow or deny) will ignore all other rules that follow it.
Network Center > Security > Firewall is the path that leads to the built-in firewall where rules can be defined.
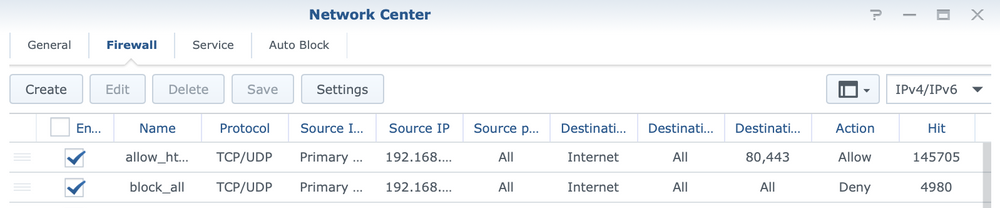
The example from the previous image shows two rules that in combination disable access to everything on the Internet (via TCP and UDP protocols) except for ports 80 and 443. As a result, any torrent traffic will not be possible.
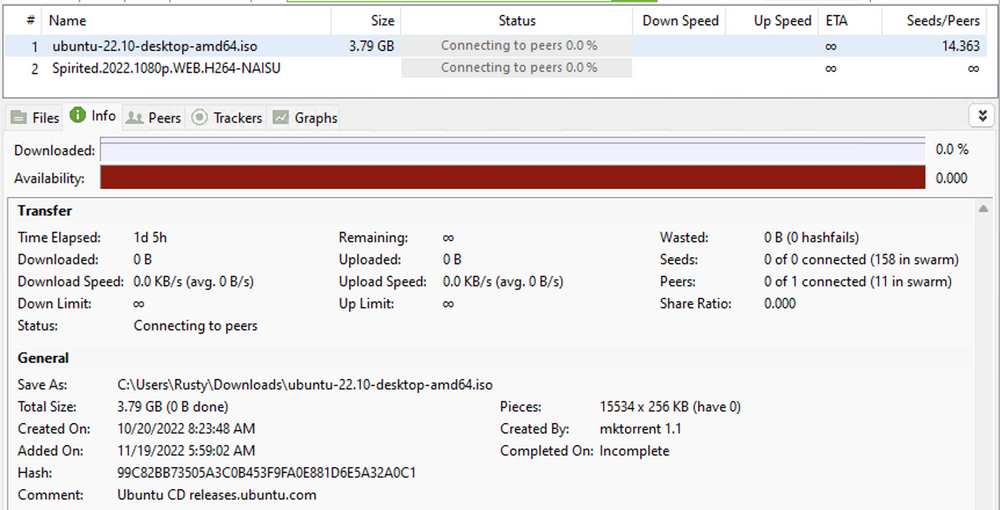
It can be seen that even after almost 24 hours there is no traffic on the specific torrent.
Next, let's see how to arrange these rules that will perform this kind of blocking. The idea is to block complete traffic to the Internet on all ports and protocols. After that, allow traffic to any specific port that is needed. It would be best to allow only ports 80 and 443 (http and https) because torrent traffic does not work on them, while access to all valid pages will be possible.
This is the only way to effectively combat all private and public torrent servers operating on various ports and protocols.
:: Firewall rules configuration
This step shows the stacking of rules that will ban all Internet traffic by TCP/UDP protocols and all ports.
The rule is configured using the following parameters:
A rule to block all traffic
**SOURCE**
PROTOCOL: TCP/UDP
NETWORK INTERFACE: LAN (select the network that includes the devices we want to block)
IP ADDRESS: Specific IP (either a single address or the entire subnet is configured)
PORTS: All
**DESTINATION**
NETWORK INTERFACE: Internet
IP ADDRESS: All
PORTS: All
ACTION: Deny
After it, another rule is configured which will grant access to all destinations on ports 80 and 443 for the TCP protocol (so no UDP).
Rule to allow traffic on 80/443 ports
**SOURCE**
PROTOCOL: TCP
NETWORK INTERFACE: LAN
IP ADDRESS: Specific IP (either a single address or the entire subnet is configured)
PORTS: All
**DESTINATION**
NETWORK INTERFACE: Internet
IP ADDRESS: All
PORTS: Custom (ports 80 and 443 are defined separated by a comma)
ACTION: Allow

As a result of these two rules, it is now possible to access all destinations, while traffic to torrent sites is blocked by the SafeAccess policy, and torrent traffic (P2P) is blocked by the firewall.
Since the traffic towards torrent peers mostly goes through high dynamic ports as well as the UDP protocol, blocking this traffic on the firewall effectively closes the data transfer in all cases.
Even if a page is not caught by Safe Access or not added manually, it is the firewall that will prevent the Internet traffic itself.
:: Real-time traffic overview
If it is suspected that the devices on the network may be accessing some pages that they should not, and we want to add them to the prohibited list, this is possible by viewing logs or traffic in real time.
Using the Network Center > Traffic Control > Monitor option, it is possible to configure the traffic monitoring for a specific device by configuring the drop-down menus.
By selecting the device, the domain and live traffic options, we will get the display as in the following image.
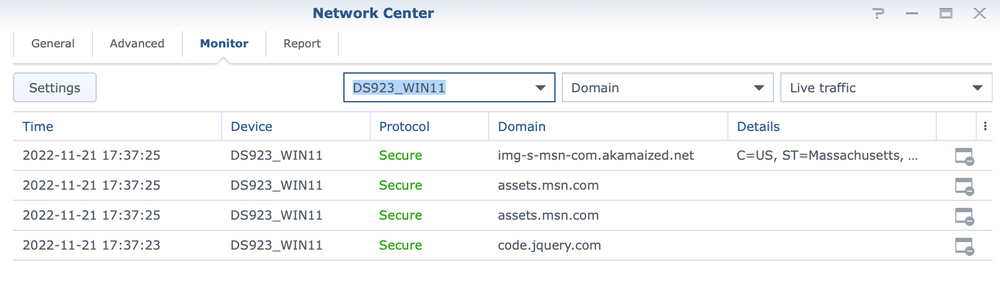
The list will show the domains and destinations that the network device accesses, and by using the icon on the far right end, it is possible to immediately add it to one of the Safe Access web filter rules to prevent its further use.
:: Special configuration for Chrome & Edge browsers
Although the mentioned process works properly, there are some exceptions when it comes to specific web browsers, such as Google Chrome or Microsoft Edge. Both of these browsers have a DNS setting in their configurations that can be turned off or on, thus completely bypassing the Safe Access settings and filtering. We are talking about DoH or DNS over HTTPS.
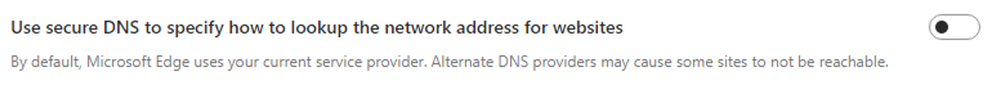
Specifically, within MS Edge, the setting is located in Settings > Privacy, and is called Use secure DNS to specify how to lookup the network address for website.
Google Chrome on the other hand has a similar setting on a similar path. With that browser, the setting is in Settings > Privacy and security > Advanced, and it is called Use secure DNS.
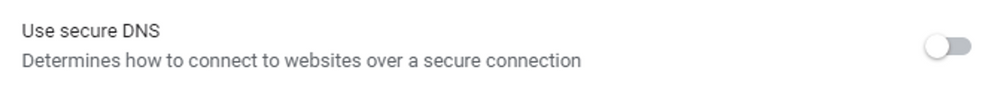
Be sure to make sure that the settings are turned off, as they are automatically turned on in newer versions of the browser.
: Conclusion
As said, controlling torrent traffic is not a trivial thing to block, so the only effective way to do it is to block the traffic on the firewall. Banning complete traffic will mean that all permitted traffic must be explicitly approved after that, but if that's the price, so be it.
Synology SRM's combination of Safe Access and firewall modules are strong enough that with a little effort and carefully collected information, it is possible to block and have torrent traffic under control, without spending more money on even more expensive routers and/or IDS/IPS/firewall specific devices.





