Synology WRX560 router review

Table of Contents
: Intro
: WRX560 - package & content
: WRX560 - specifications
: Setup and configuration
- :: SRM install
- :: SRM 1.3
- :: Network Center
- :: Mobile Internet connection
- :: VLAN configuration
- :: Security and protection
- :: Packages
: Wi-Fi support and speed tests
: Intro
This year has been very fruitful for Synology in terms of new devices coming to the market. On top of the new x23 models, back in May, we got a brand new RT6600ax router. Presented as a flagship model and with the introduction of wifi6 support, this was a clear indication that the age of AC standard has come to an end.

This does not mean that we will not be able to use the current RT2600ac or MR2200ac devices (individually or in mesh), it simply means that it is time for an upgrade. So far Synology has delivered four router models starting with the RT1900AC to the current RT6600ax.
Just as much as the MR2200ac was a complementary (but it can function on its own) device to the main RT2600ac, the same goes for the new WRX560 11ax and RT6600ax. These two models will present the new mesh setup option, while remaining compatible with the older ones as well, presuming that all devices inside the mesh are on SRM 1.3.1 or better.

Let's see what the fifth router in line can bring to the table both as a stand-alone router or as a part of a larger mesh setup.



: WRX560 11ax - package & content
With an already familiar design, the WRX560 comes in a single slim package that already speaks about many features and options this device has to offer.




With less than 1.4 kg in weight, the inside of the box contains only three things. The router itself, power adapter, and a single LAN cable.


The adapter is modular, so you can exchange the connector type with a different standard one if you have it or plan on buying it.


: WRX560 11ax - specifications
Looking at the specifications of this router it is following in the footsteps of its big brother with some changes here and there. To start, it is using a quad-core 1.4Ghz CPU, but with half the RAM coming in at 512MB. This is the same capacity that RT2600AC has.

Just like the RT6600ax, it has also two antenna types. 2T2R + 4T4R omnidirectional high-gain dipole (2.4 GHz/5 GHz) with a max speed of up to 600 Mbps for the 2.4GHz, and 2400 Mbps for 5GHz. Just like the MR2200AC, this router has no visible antennas as expected.
Supported wireless standards are 802.11 b/g/n/ax (2.4Ghz), and 802.11 a/n/ac/ax (5 GHz) just like on the RT6600ax model.


On the side and the back, are all the ports and options that come with this router. A familiar 5-port RJ45 setup with one dedicated WAN port (1G), and 1+3 LAN ports. LAN1 port can also be configured as WAN2 and just like on the RT6600ax model it is 2.5G capable. The rest of the ports are 1G in terms of maximum speeds.

The mentioned 2.5G LAN1/WAN2 port can be used with your ISP delivering multi-gig speed, or as a backhaul connection towards another RT6600ax/WRX560 device.

WRX560 also has a single USB 3.2 Gen 1 port on the side that can be used for connecting mass storage devices. The main use will be installing apps from the Package Center as well as holding the Threat Prevention database on it. This port supports USB hubs as well, so if you have one, and want to use an SD card instead, you can.
If we compare the WRX560 model to its previous generation, the MR2200ac (regardless of that WRX560 is advertised as RT2600ac successor) in terms of size and weight it is only about 80 mm taller than the MR2200ac model, weighing only 1 kg. 233 x 194 x 66 mm (H x W x D) still makes it a compact router or a WiFi access point inside a mesh setup.

Just like the previous generation, the WRX560 is a standalone device that can't be wall-mounted so keep that in mind in case that is a requirement.
Considering it is a faster device with better hardware components it is noticeably better ventilated. With no active cooling, the router has plenty of airflow gaps on every side apart from the side ones. The biggest ventilation is coming from the bottom and the top side, so consider not placing the router in a tight space to allow for better bottom-to-top air flow circulation.


The bottom side also has a total of four rubber feet that will hold the router in place and elevate it to allow air intake. With its 66 mm in depth, it is much thicker than the MR2200ac but that is the price for more air volume needed to cool the faster CPU and placement of wi-fi 6 capable hardware.

The WRX560 has no visible lights on itself other than the three LEDs on the front of the unit. With its design, it will be possible to place it in some more visible areas of your household as it also has no visible antennas.



If the design is something that is also a factor, with its rugged enclosure, and minimal lightning with no active cooling, there will be no need to hide it out of sight and potentially cause heating issues along with it.

The size of the router as well as its default vertical orientation will make it stand out for sure, so if this is the device that anyone is considering, be sure to have a place for it, as well as maybe to see it in person before getting it, just to be sure it "works with the room".

: Setup and configuration
The WRX560 comes with an SRM 1.3 version just like the RT6600ax. The device will be preloaded so the only thing left to do after it's powered on, is to connect to the router's interface (via its IP address) and finish the configuration.
:: SRM install
The router is preconfigured to use the 192.168.1.0/24 network range, specifically 192.168.1.1 IP address. Logging onto it, the initial SRM page will load up and the configuration process starts.
After the initial reboot and previous steps, SRM will allow you to configure your internet connection.
Once you have completed the above steps, log into the router using the account configured during the setup process.
:: SRM 1.3
With SRM now up and running it is time to tweak and configure it. I will not go into all the details, and elements of the OS, but rather mention parts that are both important and interesting for a wider audience.
The images reflect the main elements of the SRM that is the same across all routers that support it. In the following sections, there will be a focus on some of the major elements that SRM offers as well as how to configure them and what would be the benefit of running your own router instead of a generic ISP one.
:: Network Center
After the initial setup, we are now left with a choice to configure all the settings that this device offers. From Internet connection to local security, Safe Access, or some of the dedicated packages that offer specific functions, like a VPN server.
For the most part Internet connectivity is high on everyone's list so it would be logical to start there. The Network Center module of SRM is where most of the functions live, so it is normal to start there, and the fact that most users will spend a great deal of time there setting up and configuring.
The module is divided into much the same sections as in the previous 1.2 version with some exceptions and new features.
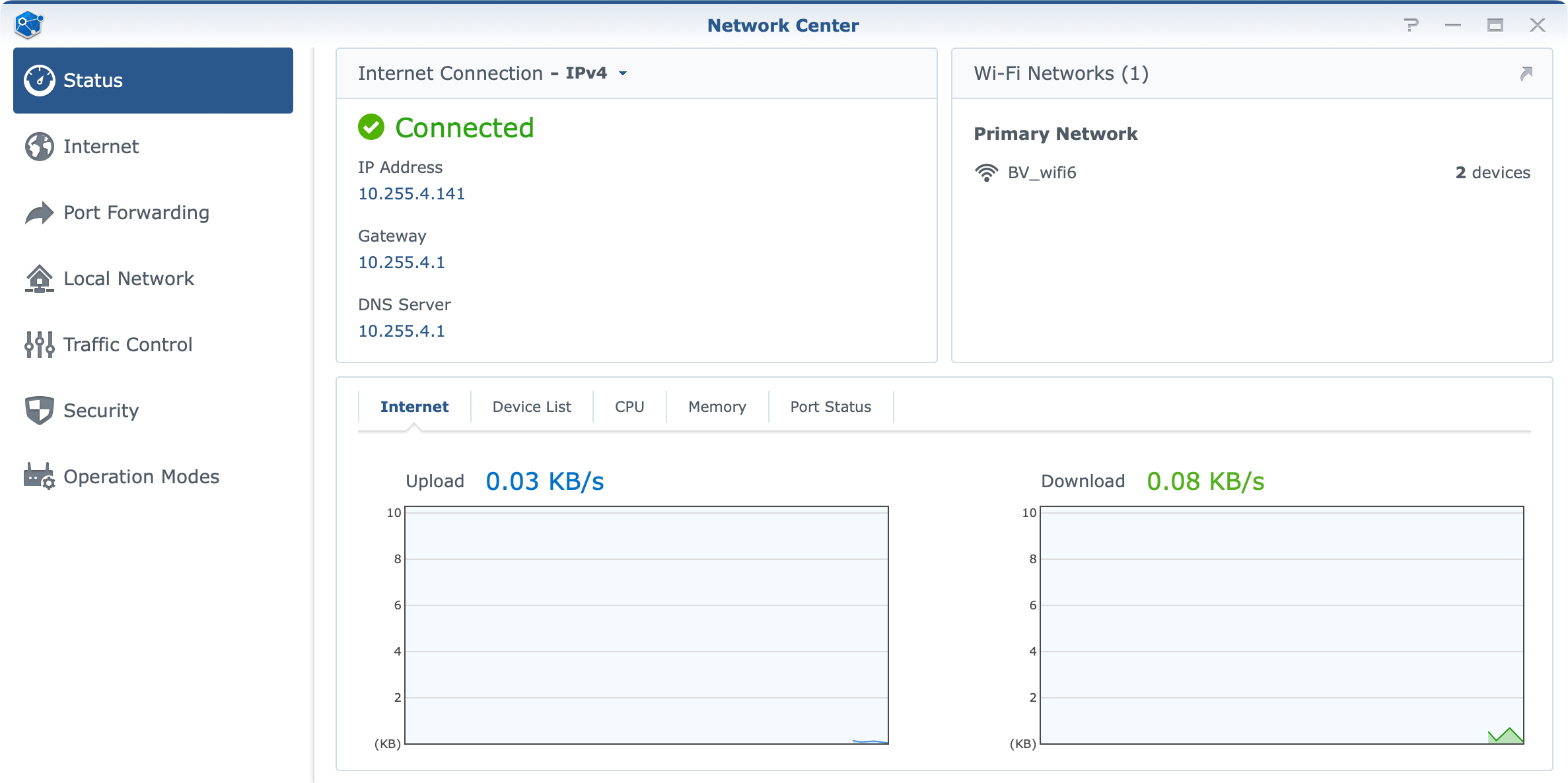
The Internet section will be the place to go and configure the needed settings in terms of Internet connectivity. This will also be a place where we can configure the LAN 1 port (WAN2), as a secondary WAN port in case we want to take advantage of the 2.5G port speed.
In general, if the initial setup wizard was used when setting up SRM, the Internet connection should be all good to go. As I mentioned earlier, we will need to have the router connected to the WAN (blue) port in the back to get this going as well as any custom ISP configuration that needs to be done.
By custom, I am referring to the usual VLAN ID value(s), especially if there is an option to directly connect the router to the ISP infrastructure without the need to use their router beforehand.
"The WRX560 was released with the same SRM version as other models. The development of custom VID for LAN1/WAN2 is still ongoing."
Mike JJ Chen
Director @ Synology
So why is this a problem? Well for my particular case, my ISP has a custom VLAN ID value that needs to be applied and it works as I said for the WAN port. But, in order to test the new 2.5G port as a WAN port, I am unable to do it as the VLAN ID is not applied and because of it, I do not have access to the Internet. Finally, I am unable to test this multi-gig port in a multi-gig ISP setup.
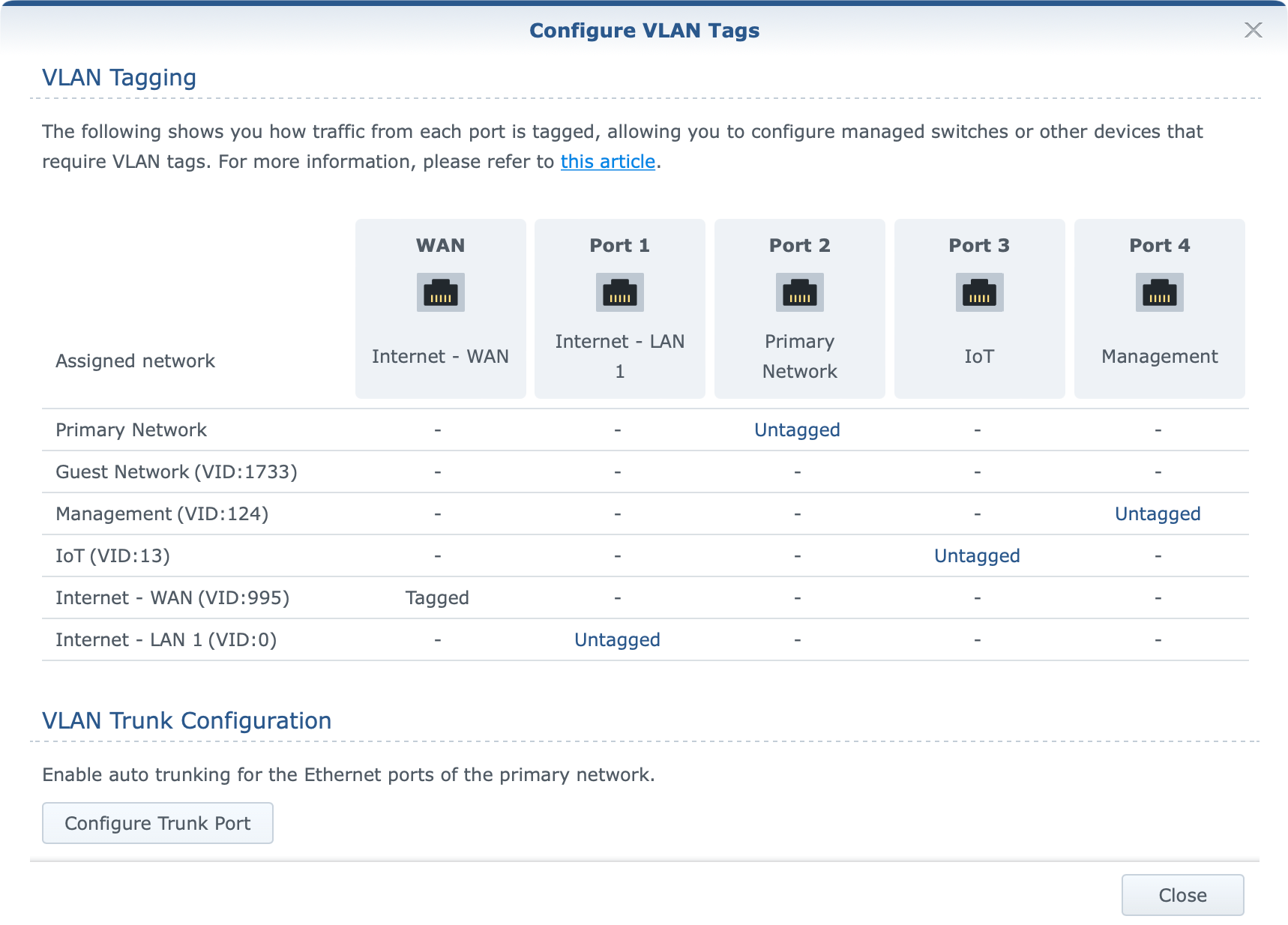
With SRM 1.3 version and VLAN support for all ports, as well as the option to make multiple networks, we now have a visual presentation of the status and VLAN ID values.
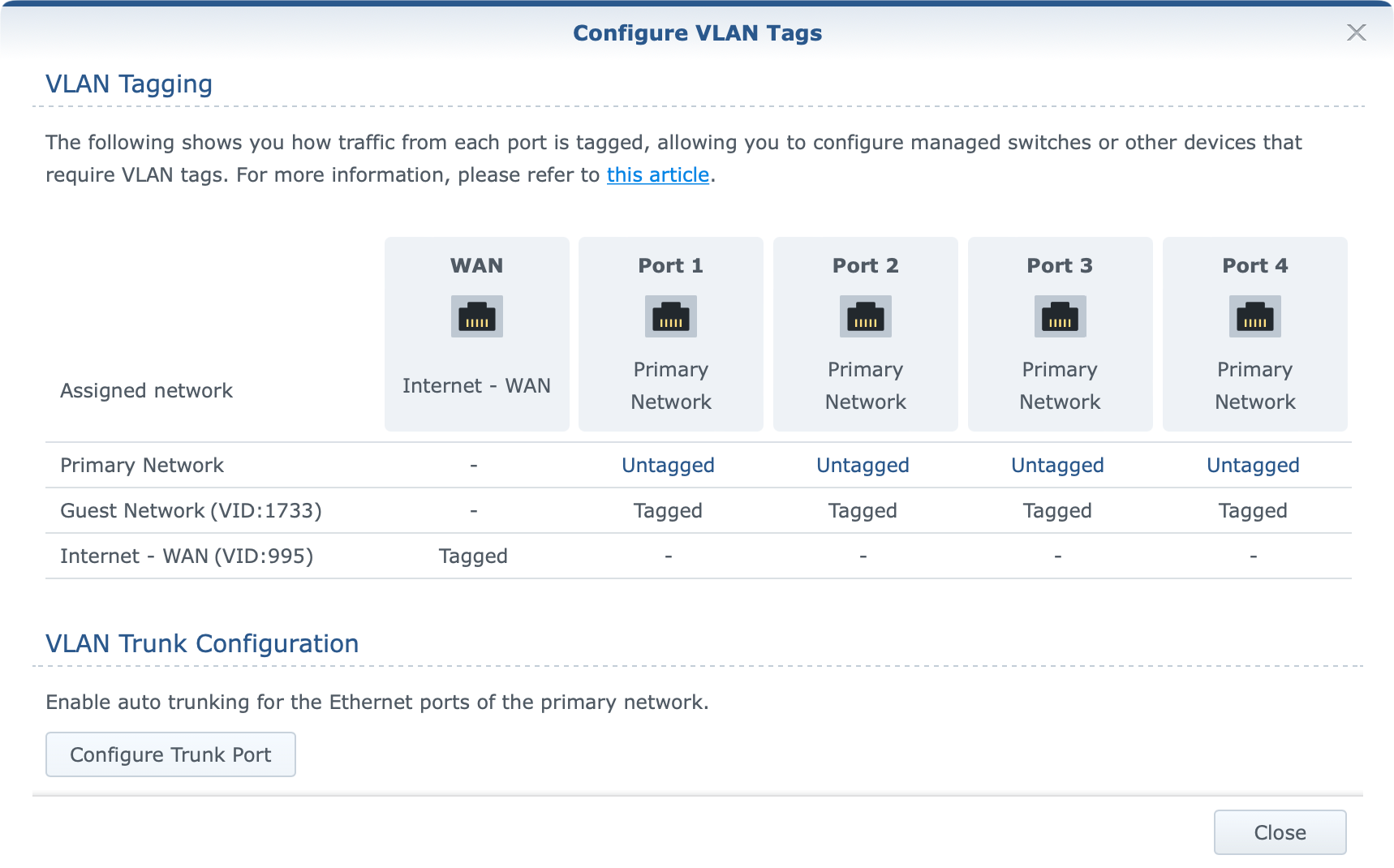
As the image presents, a custom VLAN ID has been applied to the WAN port/network and Internet access works just fine. However, activating the 2.5G port (LAN1) as the WAN port will make the following change.
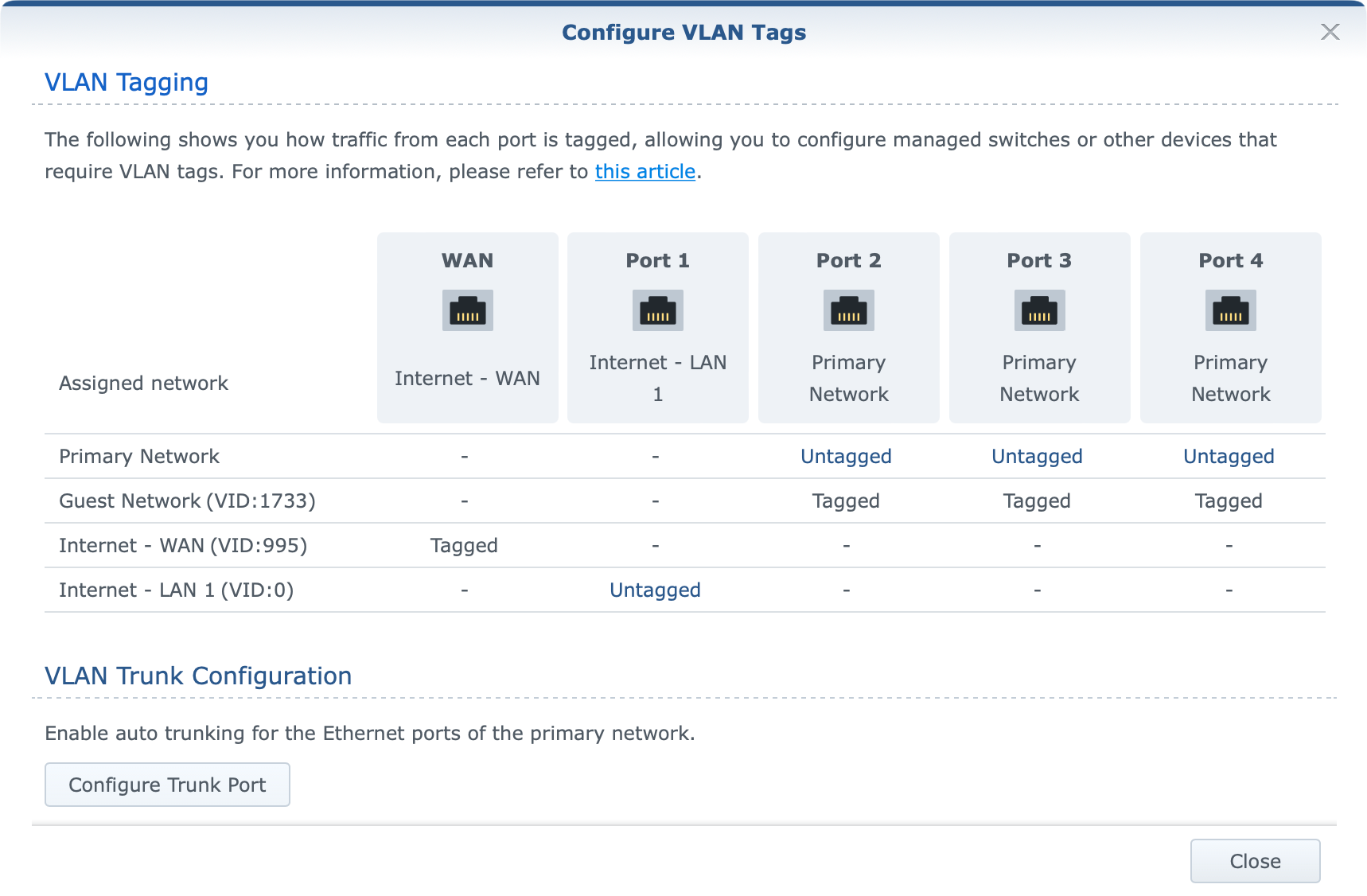
For those not familiar with how WAN tagging works in SRM the official KB explains it.
What we need to take out of it is the following:
- If the secondary interface (LAN 1) is not enabled, the VLAN ID for outgoing interfaces will be applied to the primary one (WAN).
- If the secondary interface (LAN 1) is enabled, the VLAN ID for outgoing interfaces will be applied to LAN 1.
So bullet No1 (VLAN image 1) works as intended, while bullet No2 (VLAN image 2) does not. Activating LAN1 as your WAN port should apply the same tag ID to it and not leave it untagged (value 0). This matter has been reported to Synology, and hopefully, it will be corrected in the future.
So at the moment, while you can without any problem utilize your WAN port with full 1/1G speeds (more on that later) from your ISP those looking to utilize the 2.5G port as their ISP incoming WAN access will not be able to do it in case there is a need to apply custom VLAN ID values to it.
As said before, this is a pending update to the SRM that will allow a custom VLAN ID to be applied to the LAN1 port then proclaimed as WAN.
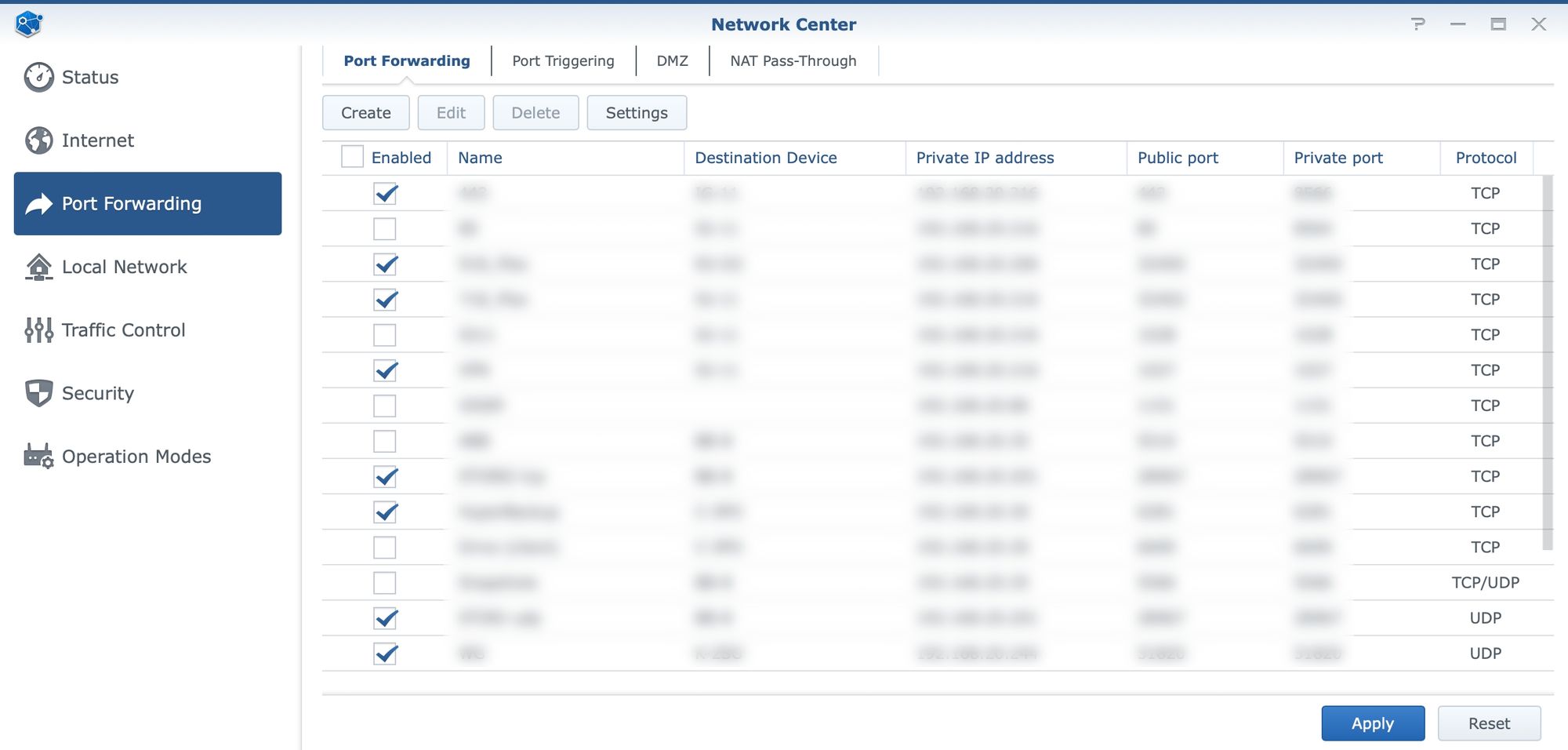
Port forward
Depending on the services running inside your home or business, there might be a need to open some ports at some point in order to utilize those services across outside networks, like the Internet. For that to work, we need to be able to port forward specific ports and protocols.
With a general ISP router and the ISP choice, there are situations where some providers do not allow for such scenarios. In case that is not the case and we can indeed provide access to services from outside the local network, port forward is one thing that will need to be configured to make it happen.
Inside Network Center and under the port forward section there is a table of settings that will allow for the configuration of various rules covering specific ports or even a range of ports.
Security
While controlling the network traffic, DHCP pools, and other elements is also possible using the Network Center, here is one more important element that could use some attention.
Closely integrated with port forward, the Security segment will offer some general security features like DoS protection and Auto-block, as well as firewall settings.
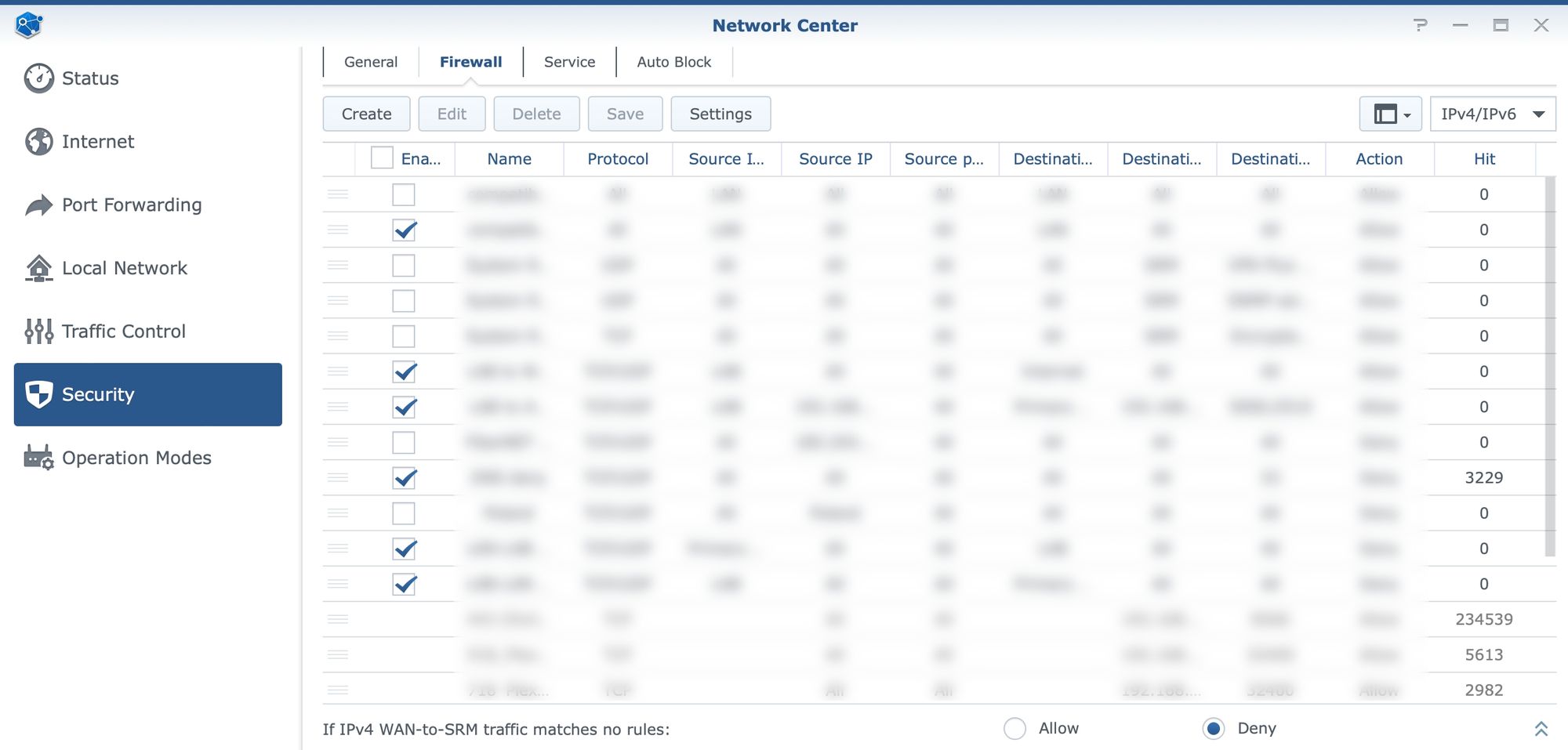
Keep in mind that while we are able to configure various firewall rules, there might already be some in case there is port forwards configured. The reason behind this is that any port forward rule will also become a firewall rule that is not possible to change from the firewall section, so just keep that in mind.
The interesting counter inside the firewall element is also a number of hits. This will show if and how often some port (or range) is being hit. Important to remember as with all firewalls is that rules are applied from top to bottom. So if we want to block or allow certain traffic the list needs to be sorted to pass over "allowed" rules first, and then move into blocked ones.
Operation modes
Another set of options in the Network Center is listed under operation modes. All Synology routers can operate in two major modes. Wireless router, or wireless AP (access point). Depending on the need the device can be configured or reconfigured as needed. As seen in the initial images in the article, SRM setup will offer the option to choose how the device will be configured. If for whatever reason there is a need to change the way the router needs to function, these are the options that will make it happen.
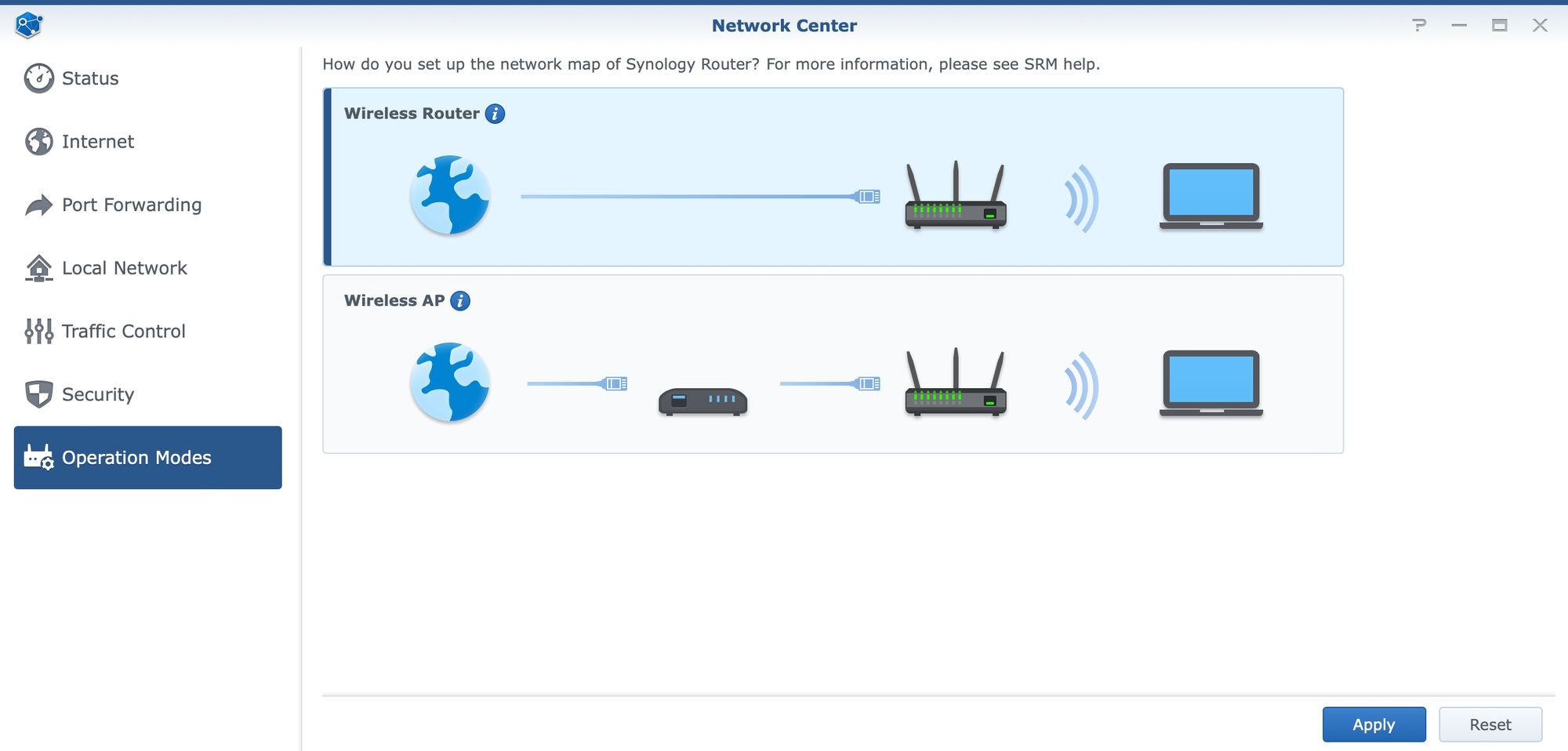
WRX 560 or any other model, will default to the router mode. In this mode, SRM will offer full services that it has unlike when the device is in AP mode. AP will not offer port forwarding or traffic control of any kind, and all ports will be trunk ports as members of the primary network.
:: Mobile Internet connection
Going back to the main section of the Network Center and Internet connectivity, there is also one thing that some users might find interesting. Mobile Internet connection.
SRM on WRX560 offers the same feature as any other device in the lineup. In case there is a need to set up a failover or load-balance scenario when accessing the web, it is possible to configure such setup once the secondary Internet connectivity is detected.
In this case, a single USB port on the router can be used to connect a mobile 4 or 5G stick that will provide an alternate connection route in case the main link goes down. Also, it can be configured to balance certain traffic over the faster link, while pushing the rest over mobile.
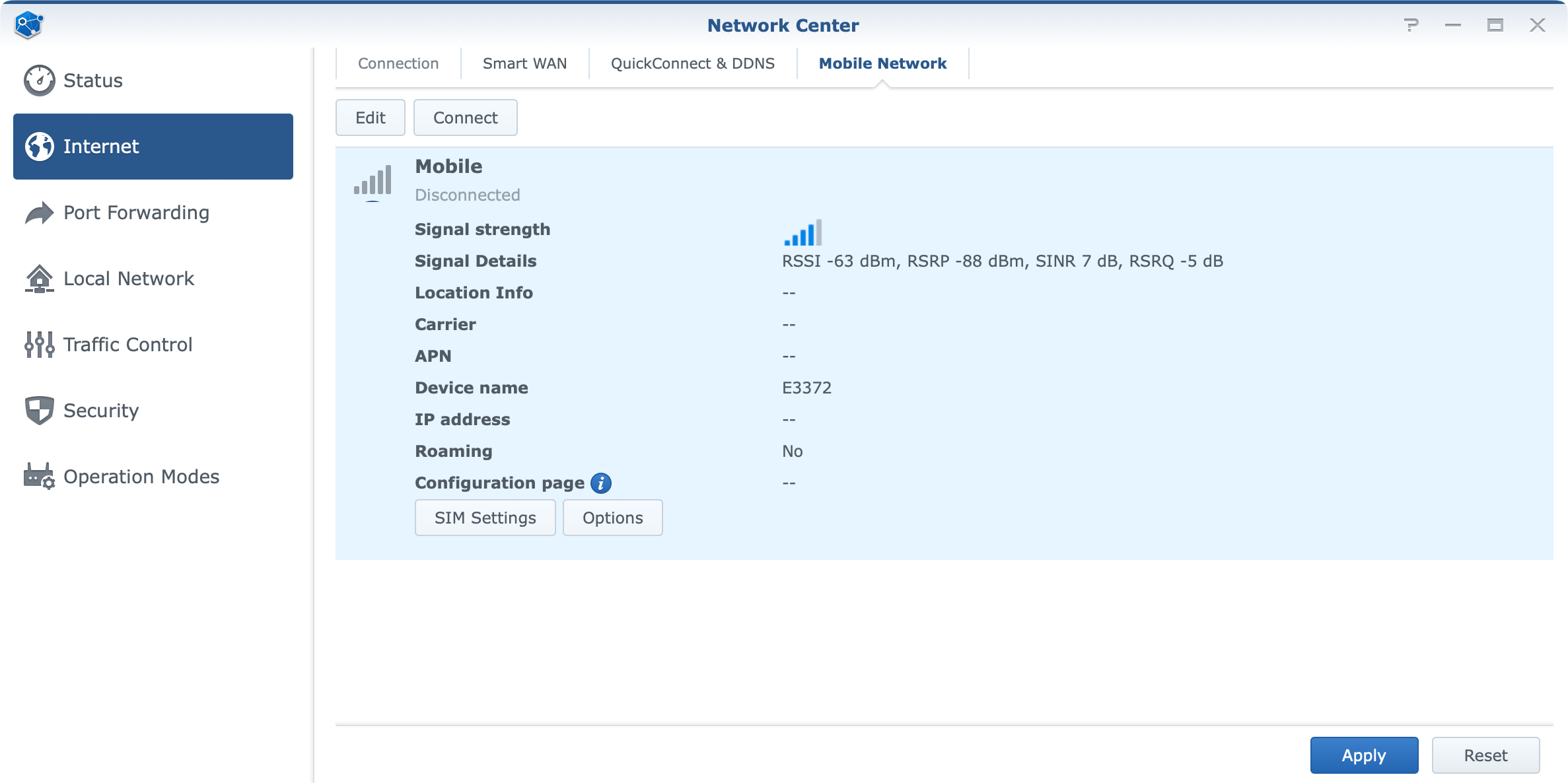
As with previous models, WRX560 was tested with Huawei E3372H-153 USB stick. ISP speeds, disconnects, and everything else that comes along with using a mobile internet provider will depend on your specific situation, but in the end, there were no issues in using a 4G connection.
:: VLAN configuration
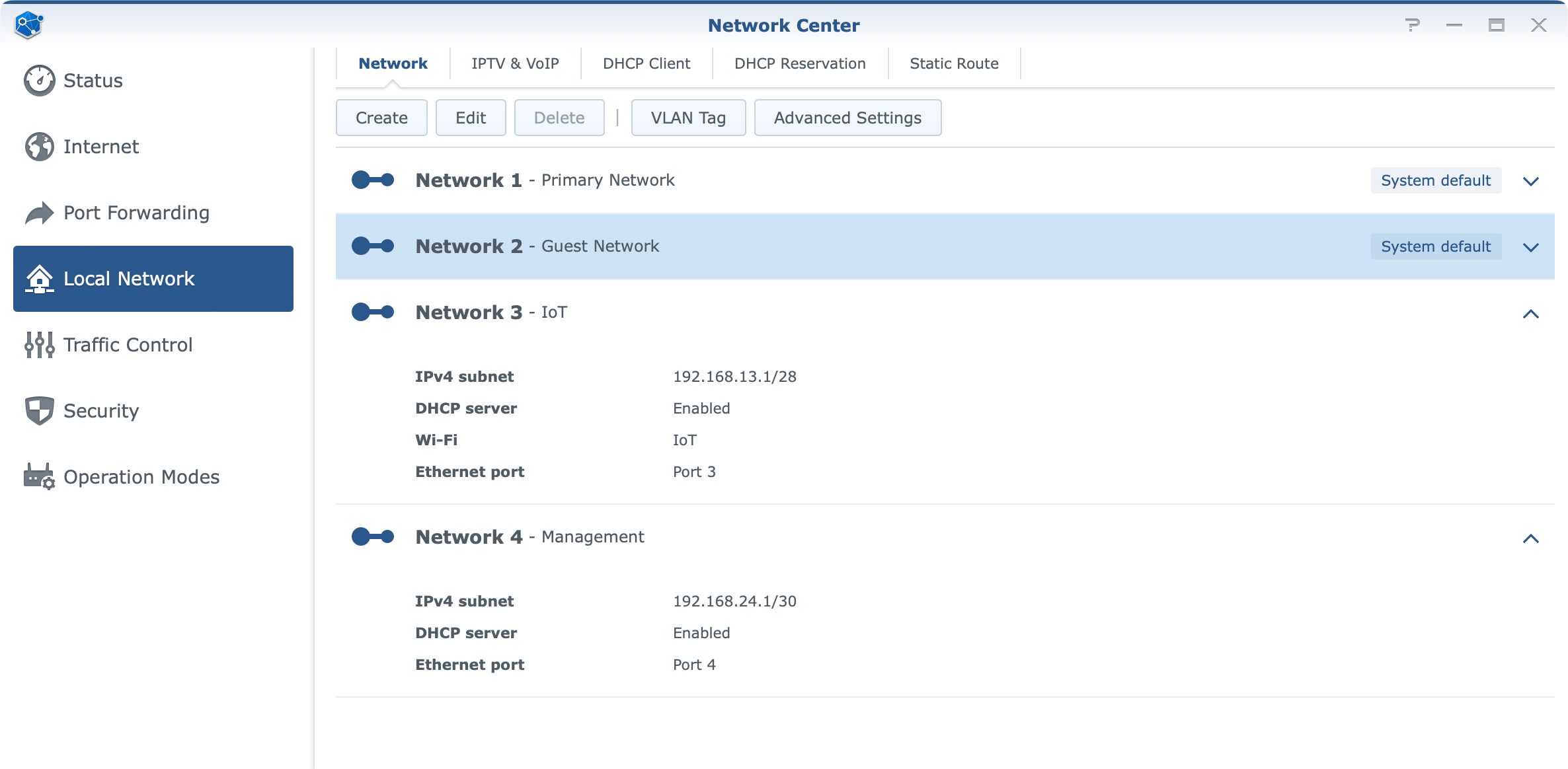
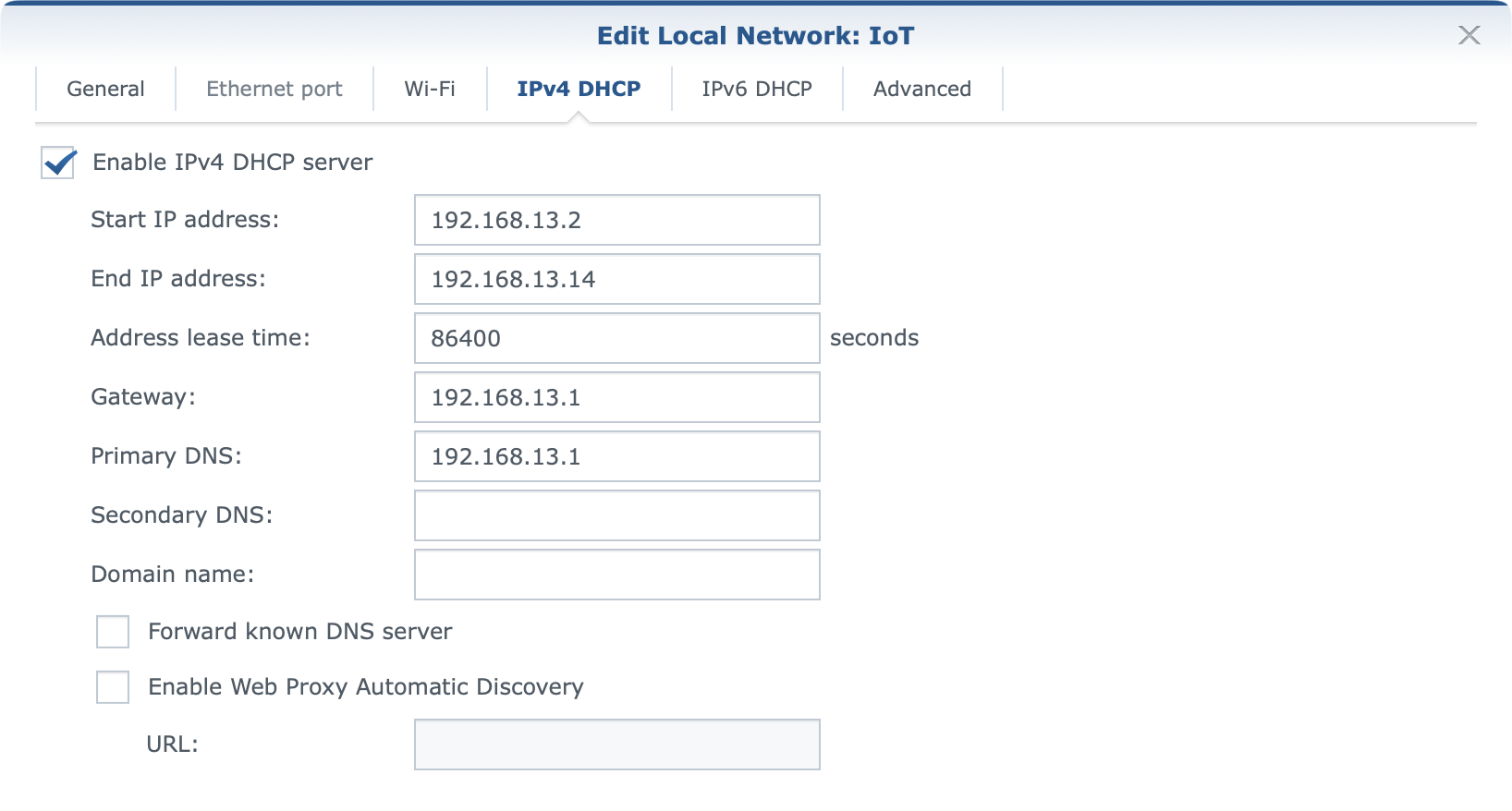
Considering that the main feature of SRM 1.3 is VLAN support it is worth mentioning it in a bit more detail. While setting up custom ID tags for a potential WAN2 configuration towards a supported ISP, we might get in contact with VLAN tagging, the case in which we will be configuring it is when there is a need for a proper network separation.
With up to 5 separate networks (4xLAN ports + guest network) there are options to divide the network any way that is needed, allow or deny access between them, as well as assign WI-FI networks and DHCP pools to them.
Support for VLANs offers a way to make only wi-fi networks with no LAN ports attached to it, or the option to add one or more ports depending on the need.
In order to further configure ports and tags for a specific network, there is a VLAN Tag button that will open and present the current state of VLAN tagging as well as offer configuration of trunk ports.
Each network by default has Internet access using the default NAT settings but all configurations can be changed at any point.
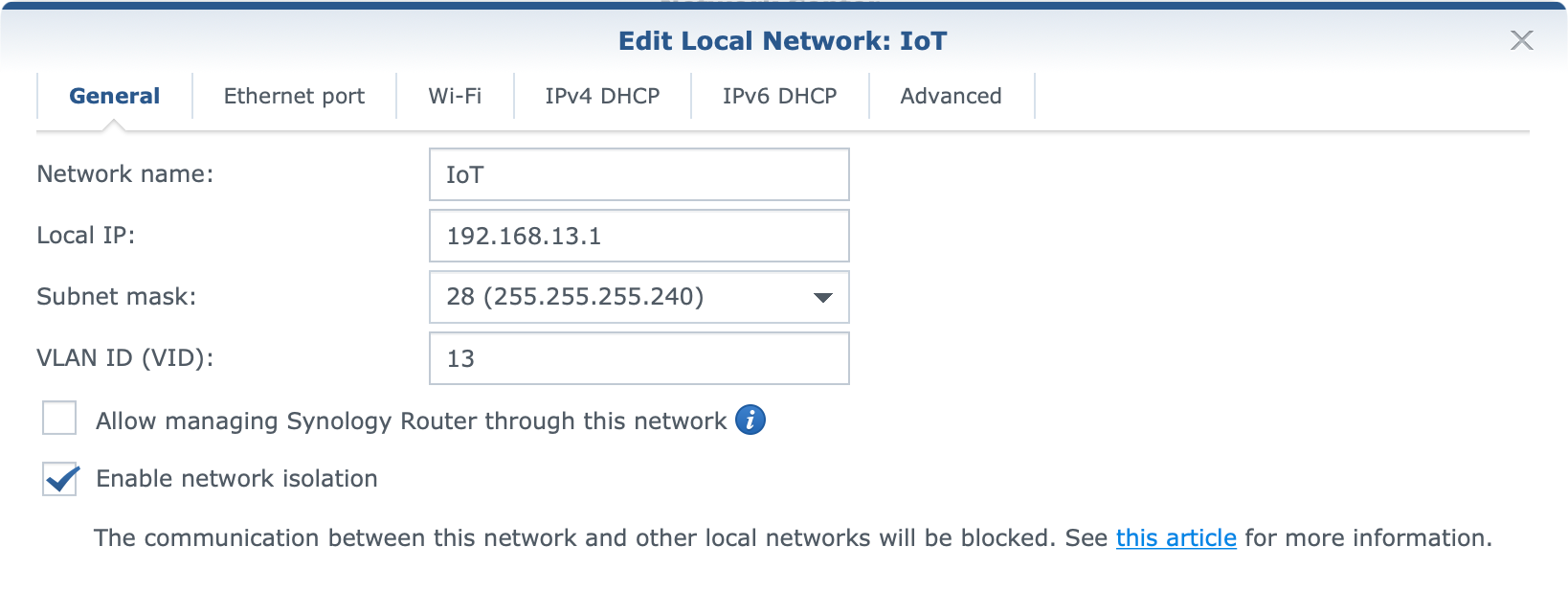
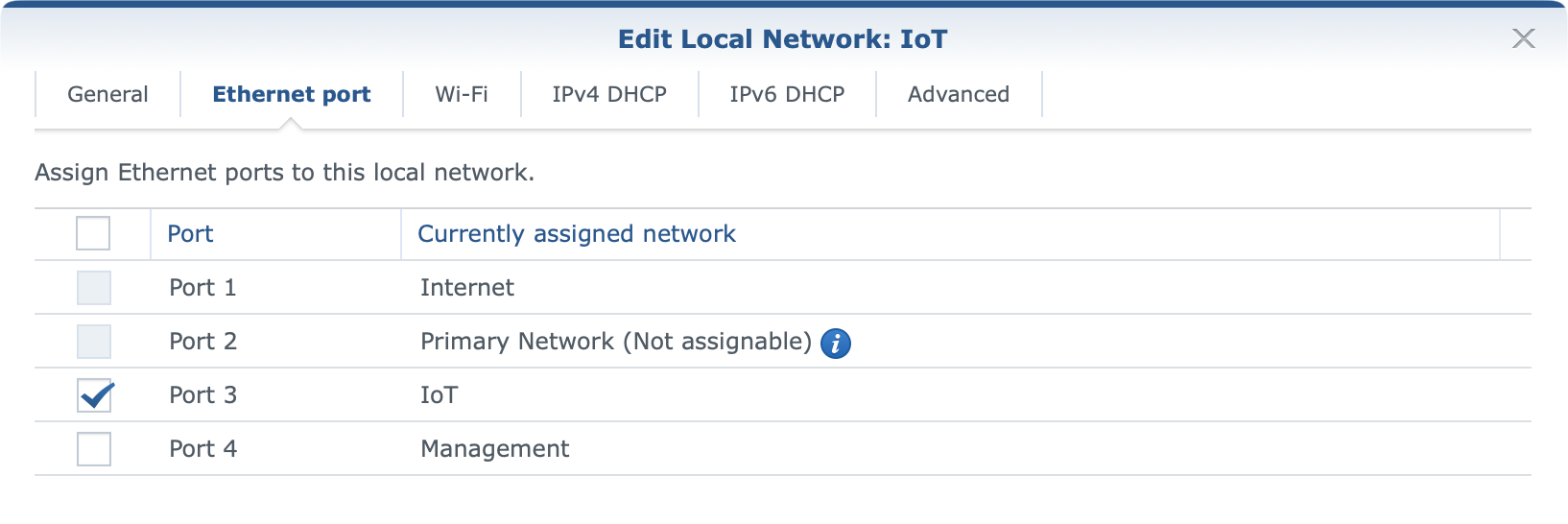
Configuration is straightforward, and in case there is any help needed on the matter Synology's knowledge base will offer all the needed help in configuring the exact setup.
:: Security and protection
In the previous sections there were some mentions of security elements that are a part of SRM by default, but here let's focus on those in a bit more detail, as well as see what else WRX560 and the OS can offer in terms of protection.
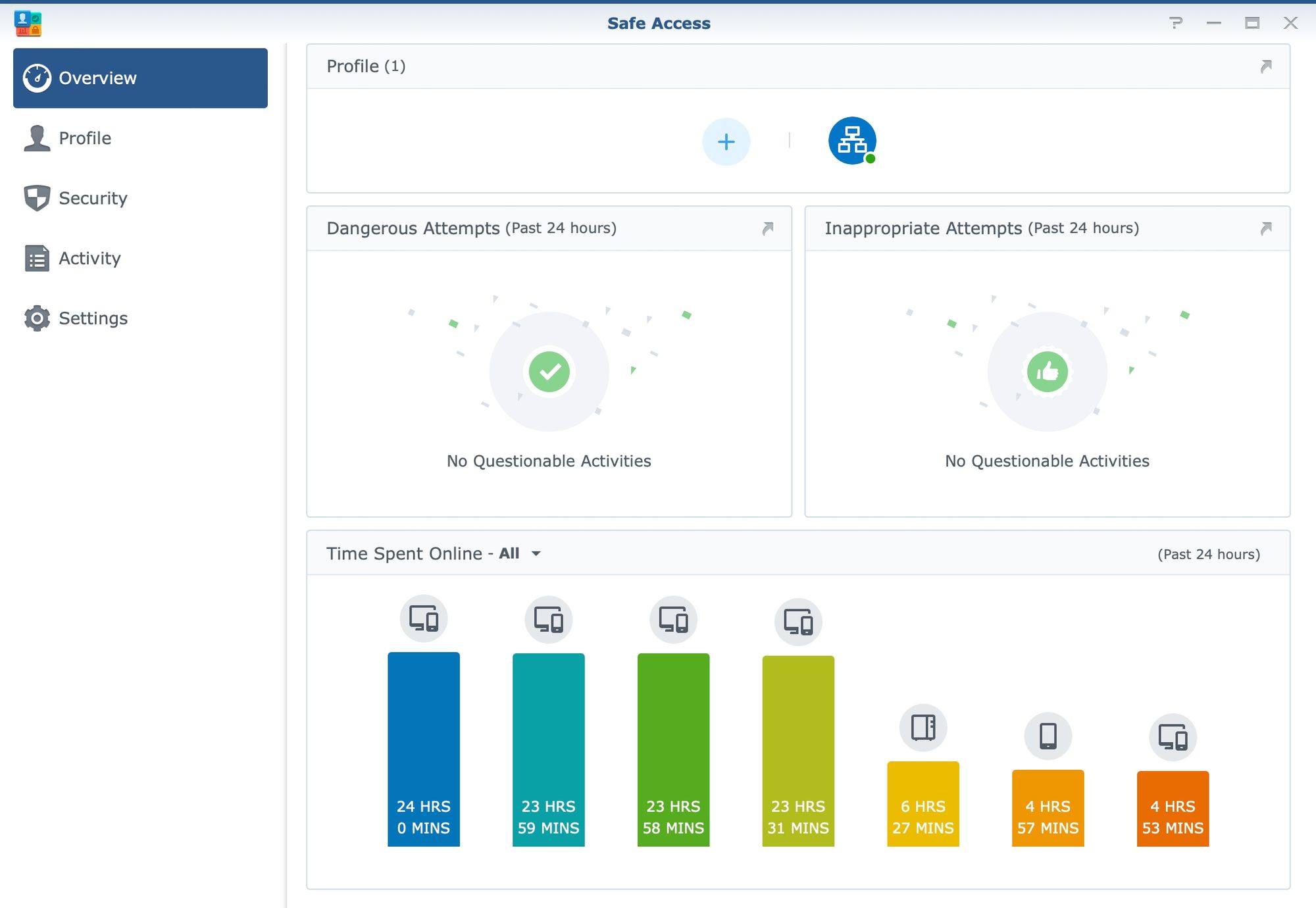
Basic elements that SRM offers in terms of security would be a firewall and auto-block options as main features of the Security section inside the Network Center.
On top of those, by default SRM also comes with Safe Access (installed by default), as well as an optional Threat Prevention*.
A firewall offers the main line of defense in terms of allowing or denying traffic to and from the internal network so be sure not to poke too many holes in it (zero if possible) to make communication with the outside world as secure as possible.
Auto-block option will be there to prevent brute-force attacks and black-list the remote IP addresses that the attacks are originating. A blocklist can be exported and cleared and individual IPs removed as well in case there is a false positive case.
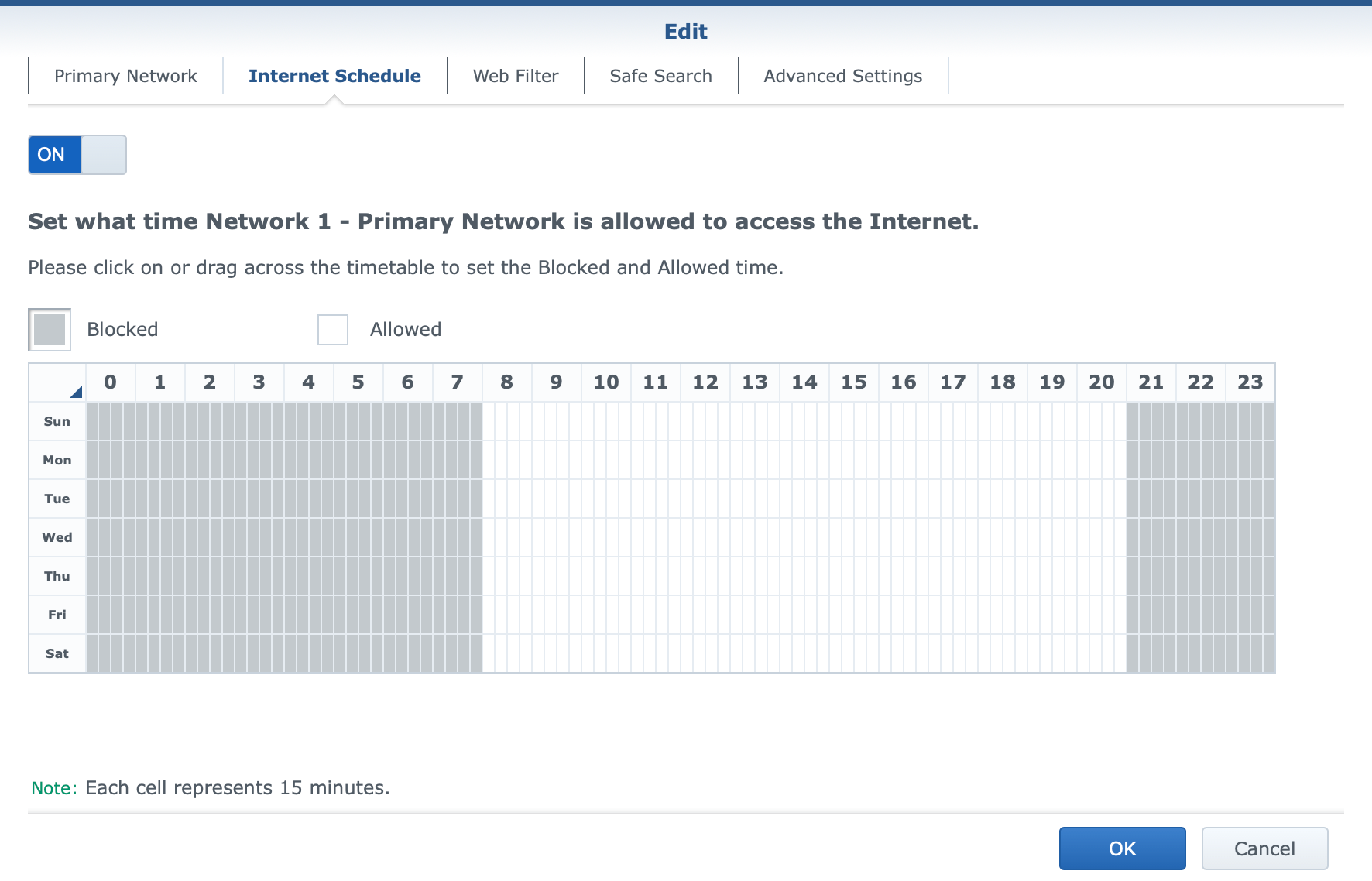
On top of those common tools, SRM offers a few proprietary tools such as Safe Access and Threat Prevention to further protect devices and LAN users from malicious websites and content, as well as to make sure that LAN users will not visit unwanted material or have Internet access outside curfew hours.
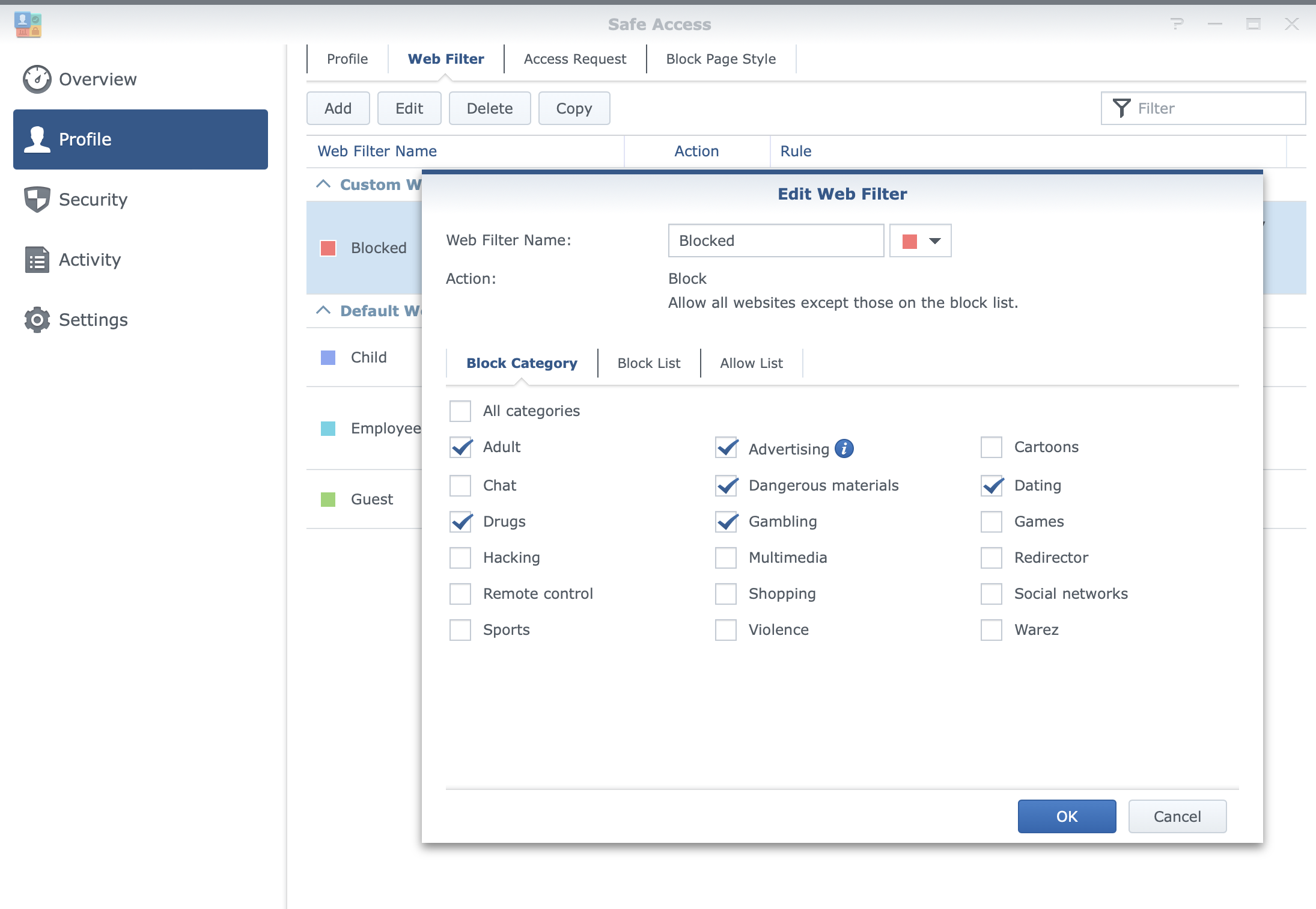
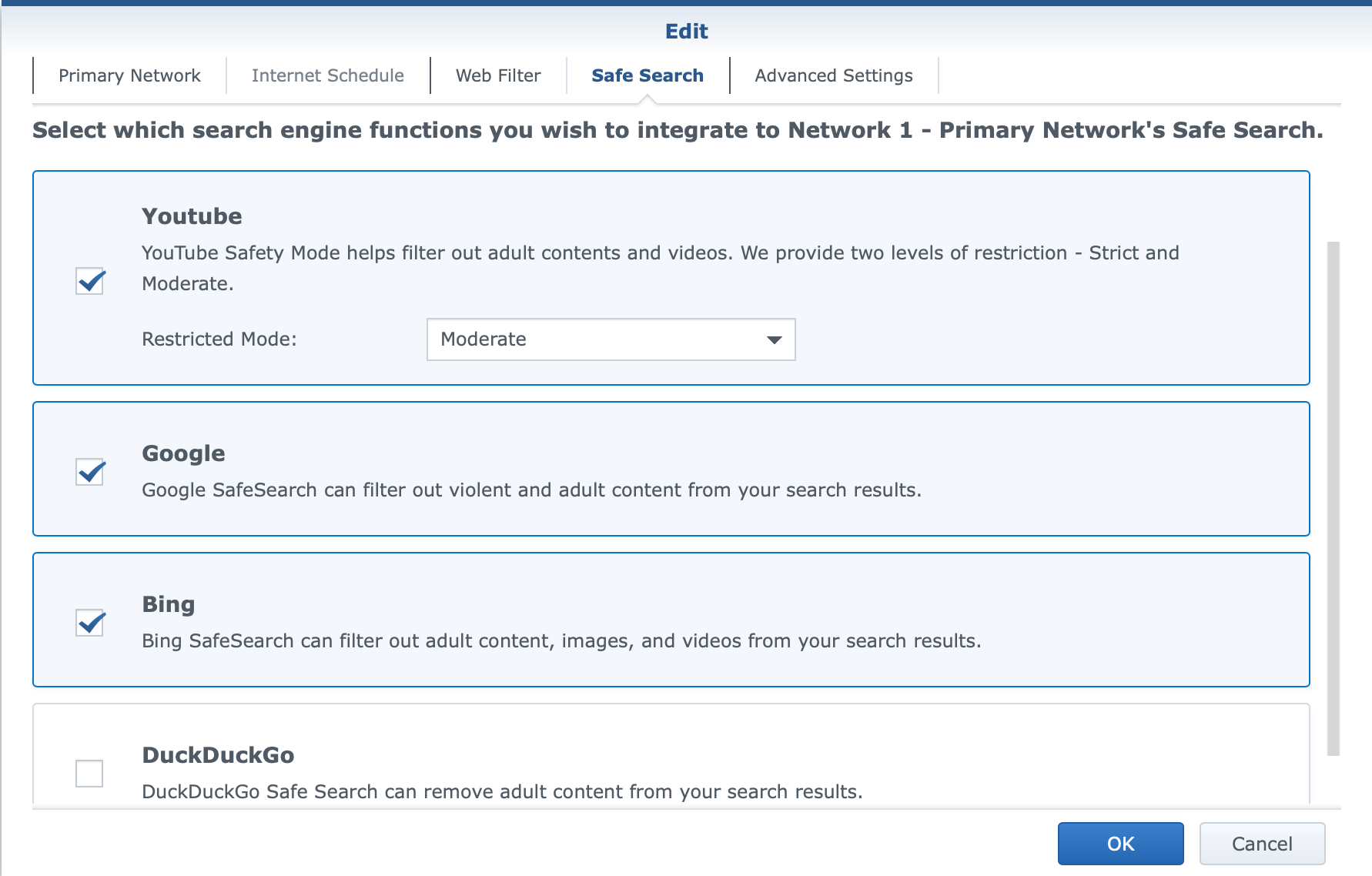
With Safe Access, there will be options for web filtering using 18 categories of websites that can be active per profile (LAN or user), as well as safe search filtering with YouTube, Google, and Bing platforms. The platform also offers parents to keep tabs on their children's Internet use by monitoring their browsing in terms of what devices are used and what content the child is consuming.
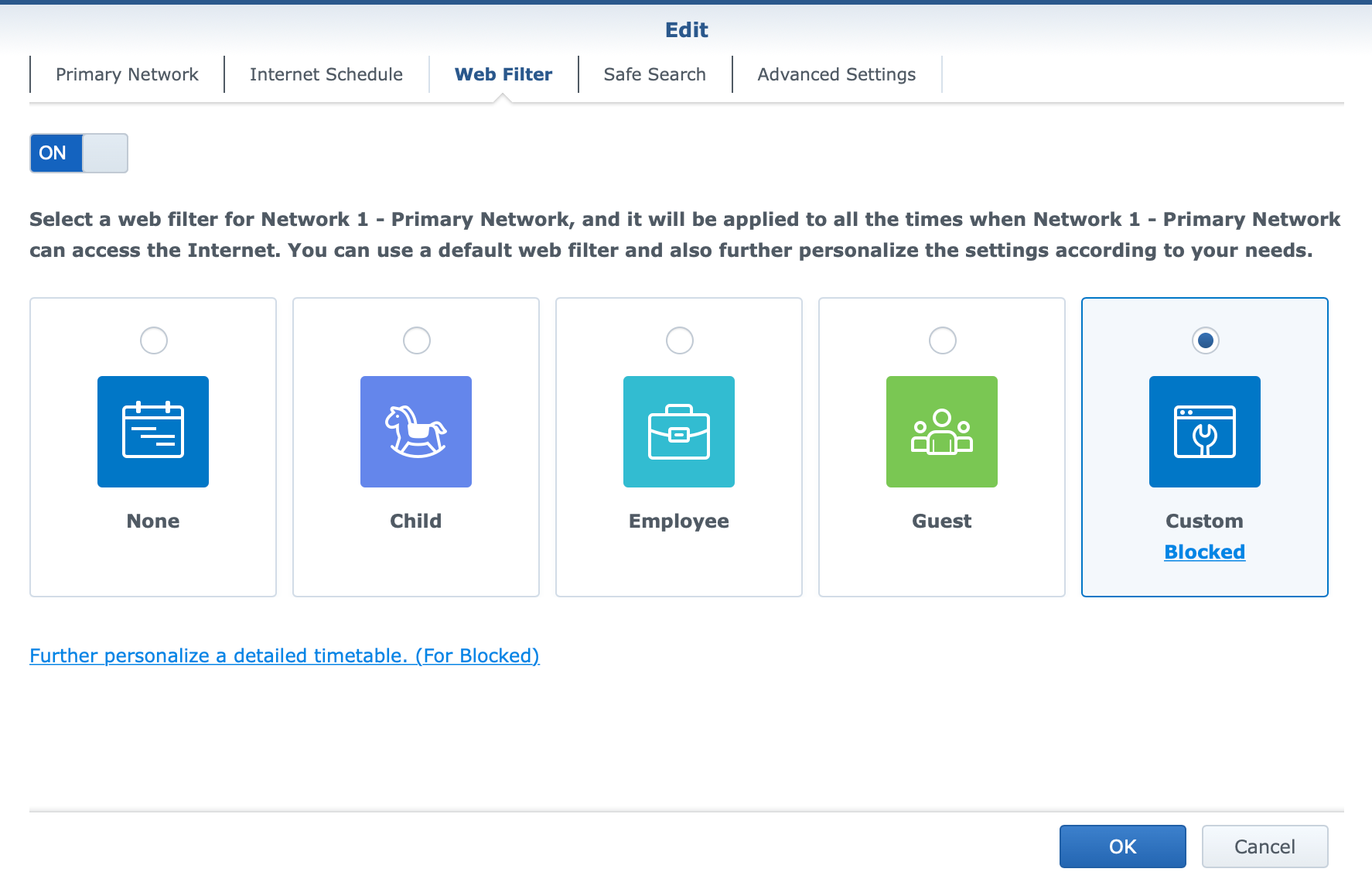
Threat Prevention tool has been around since the first router model (the RT1900ac in 2016) and has evolved a bit along the way. The principle remains the same as the main task of this solution is IPS/IDS (Intrusion prevention/detection). While using a bit more resources than when the platform is not running, TP will increase the security of the networks while invoking a certain degree of speed penalty. This is to be expected as each network package is being inspected for both incoming and outgoing traffic.
However, saying this, running this package had zero impact on the browsing speed, and the CPU/RAM of the router was also not affected.
In some cases, TP can behave "aggressively" but it can be configured to prevent such behavior in case access to certain resources starts to become problematic. With automatic updates of its database, it will be a valuable asset in the protection of internal resources.
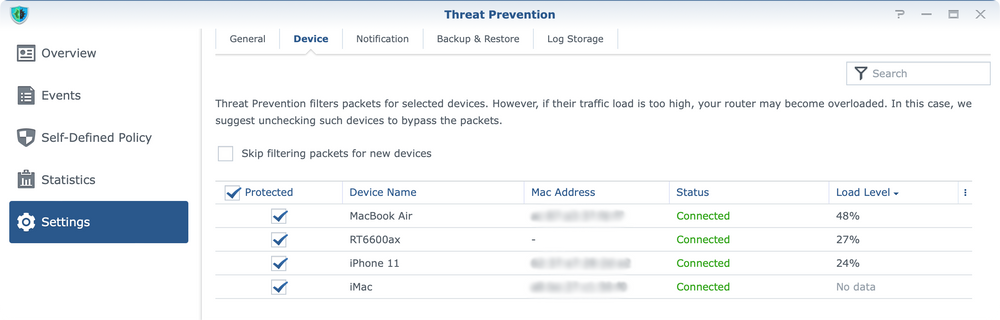
One thing to note here is that while it is an optional package it will require an SD card (via USB hub) or a USB storage device attached to the router. The reason behind it is that its database and configuration parameters will need a place to be installed, and external devices will be it. It is worth noting that faster devices will be beneficial in this case as the inspection on its own has a speed penalty already. So make sure to use the fastest possible (and compatible) device to ensure adequate speeds.
Along those apps, there is also an option to use the VPN Plus package for secure and fast access to local networks over a secure Internet tunnel.
With the rise of hybrid and remote work, usage of VPN as a method of connecting back to LAN and its resources from a remote location has been in high demand. While being nothing revolutionary, there are some benefits of using the VPN Plus solution as an optional part of the SRM OS.
VPN Plus offers configuration of some industry standards as well as some proprietary solutions by Synology to offer and cover all the possible scenarios when one might want or need to use a VPN connection.
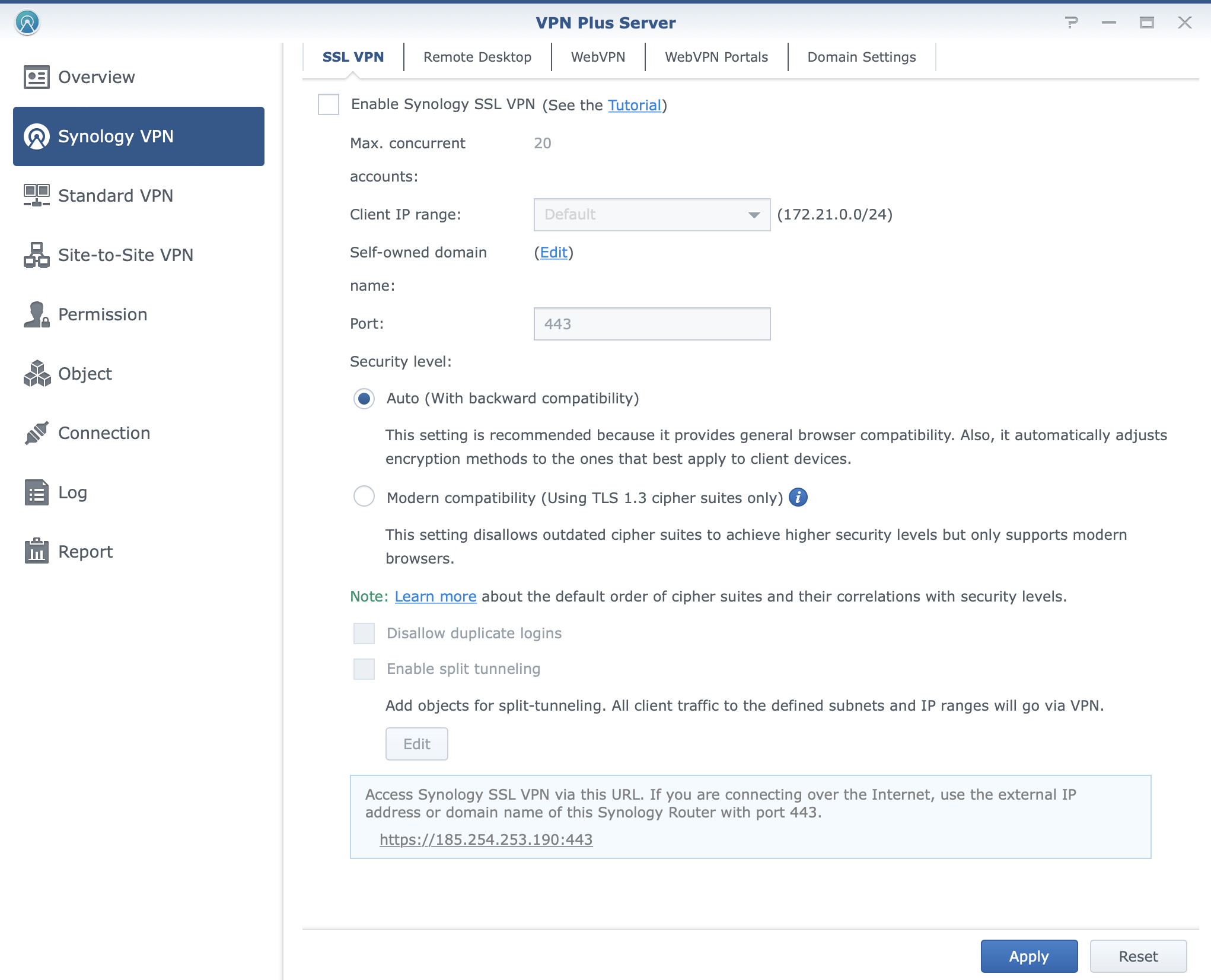
With support for SSTP, OpenVPN, IPSec, and their own Synology SSL VPN, users will have the option to use any supported device in order to install a compatible VPN client and connect to their internal services. If that is not the option, a clientless version of a VPN connection is possible where users will land on a publicly accessible portal, authenticate and get access to internal resources via a secure connection. This is possible with the use of Synology WebVPN solution.
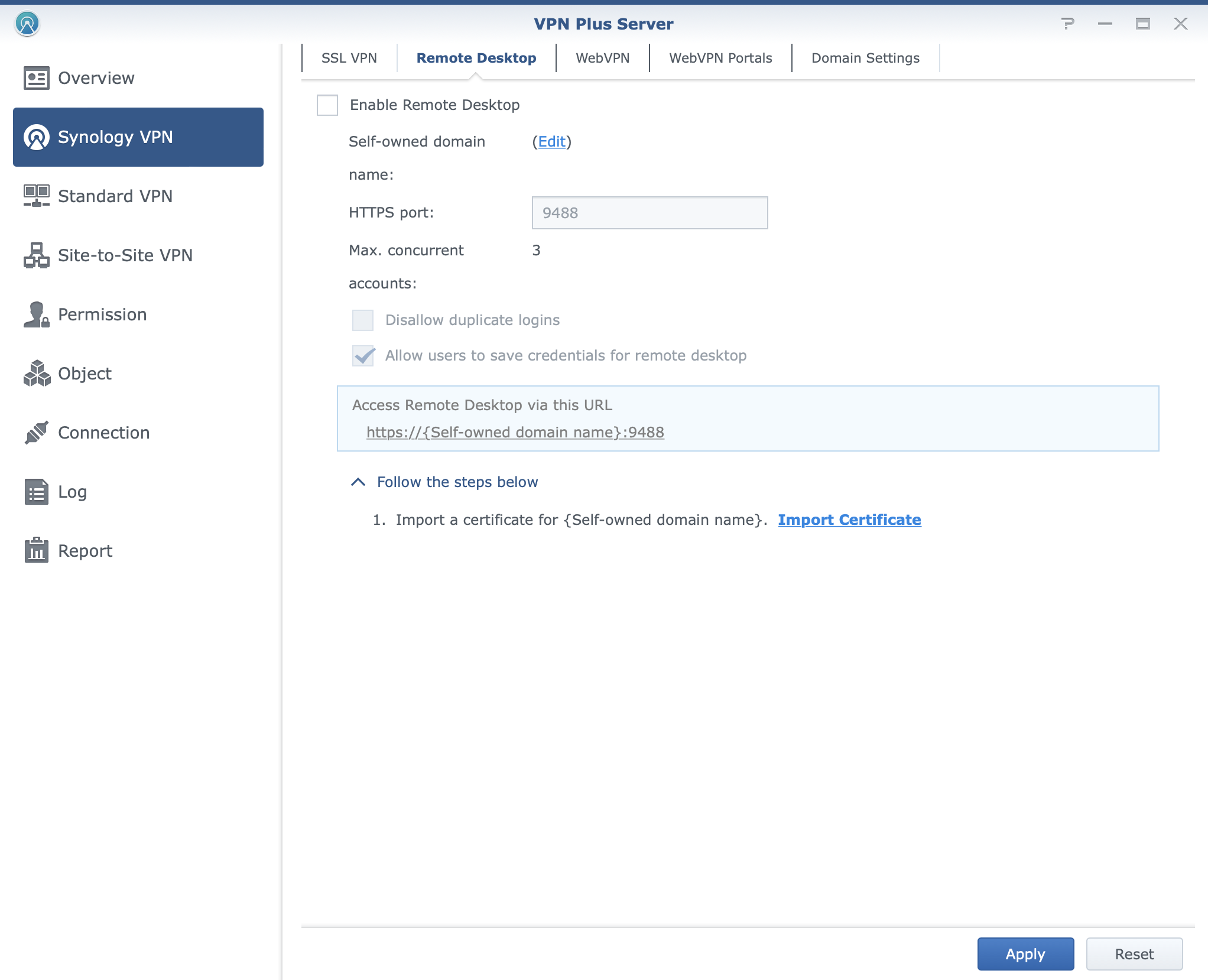
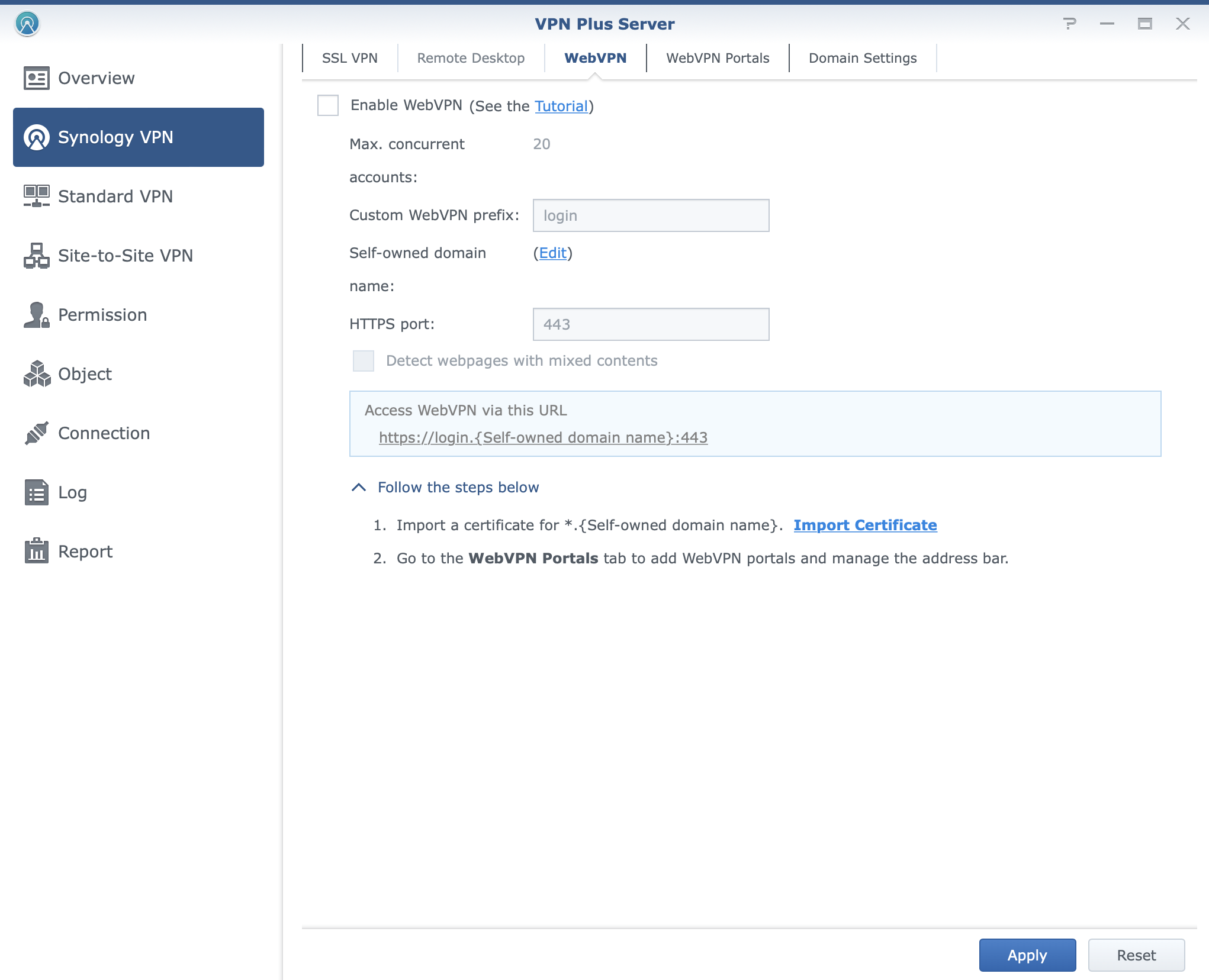
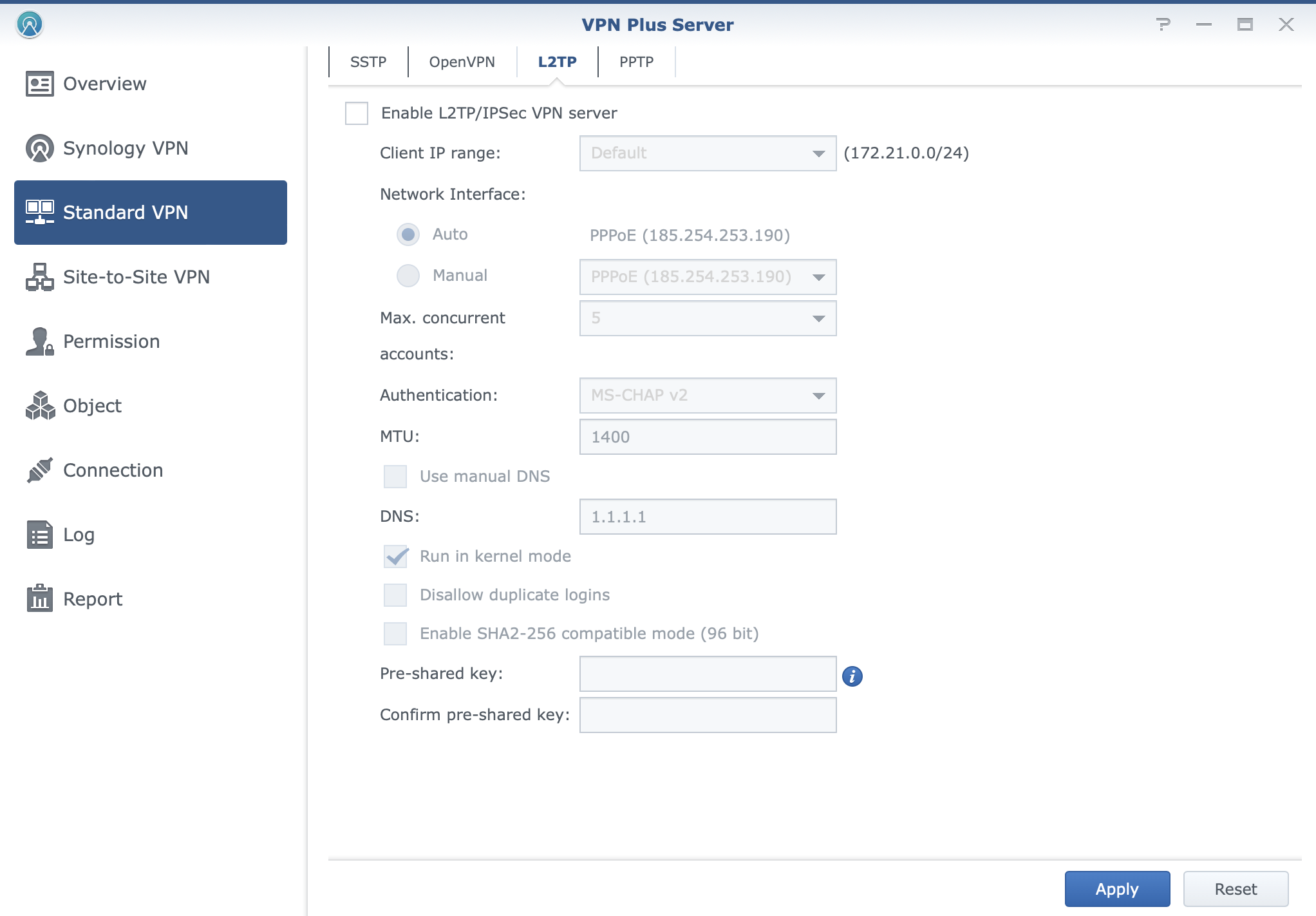
VPN connections over VPN Plus will also offer web-based remote desktop and platform-agnostic solutions using their web browser.
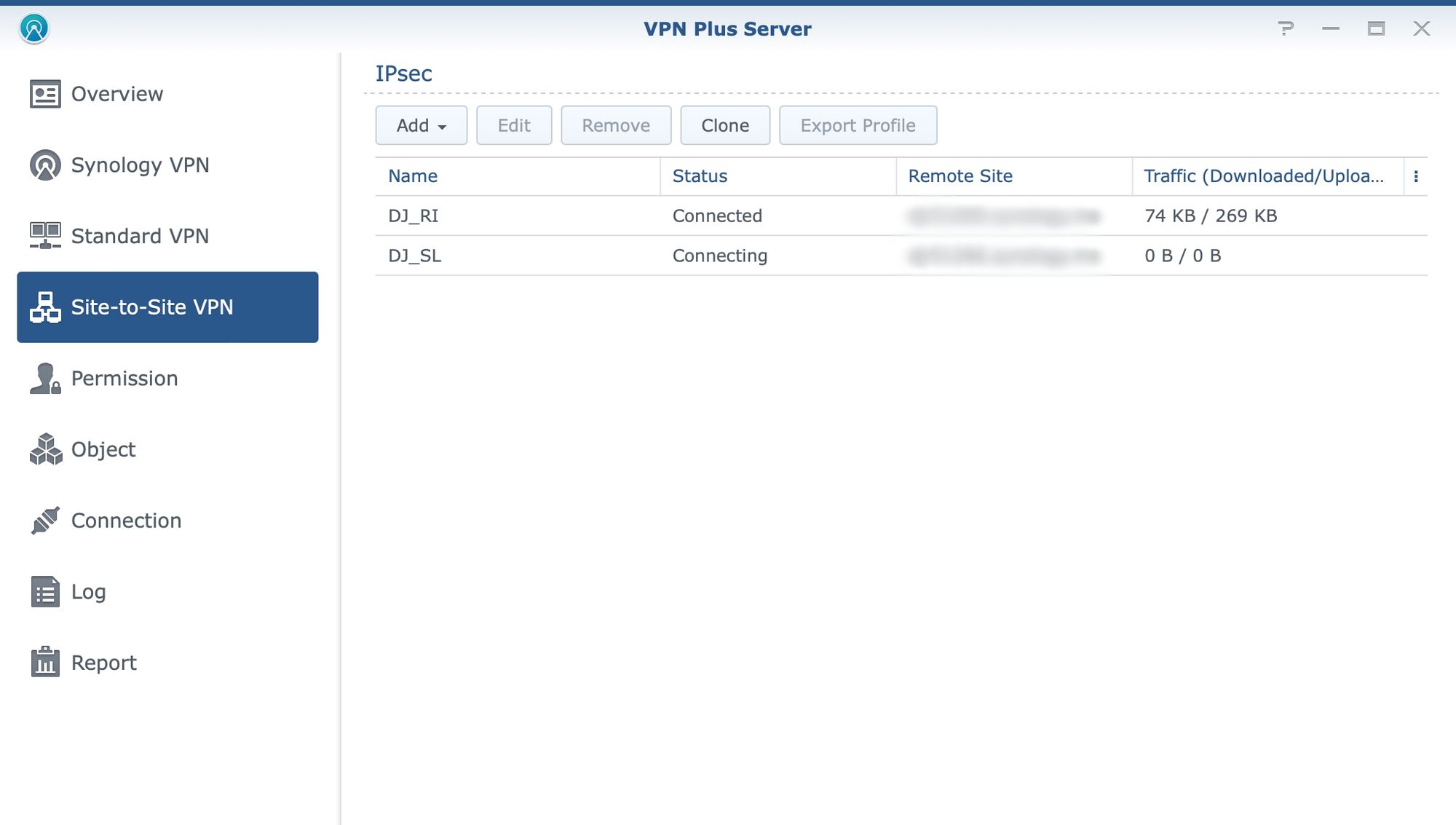
Finally, VPN Plus also offers site-to-site VPN solutions in case there is a need to stretch LAN over the Internet and offer a protected secure tunnel with access to all local resources without any additional VPN configurations for the user. For more details on the actual implementation of this scenario be sure to check the following article.
:: Packages
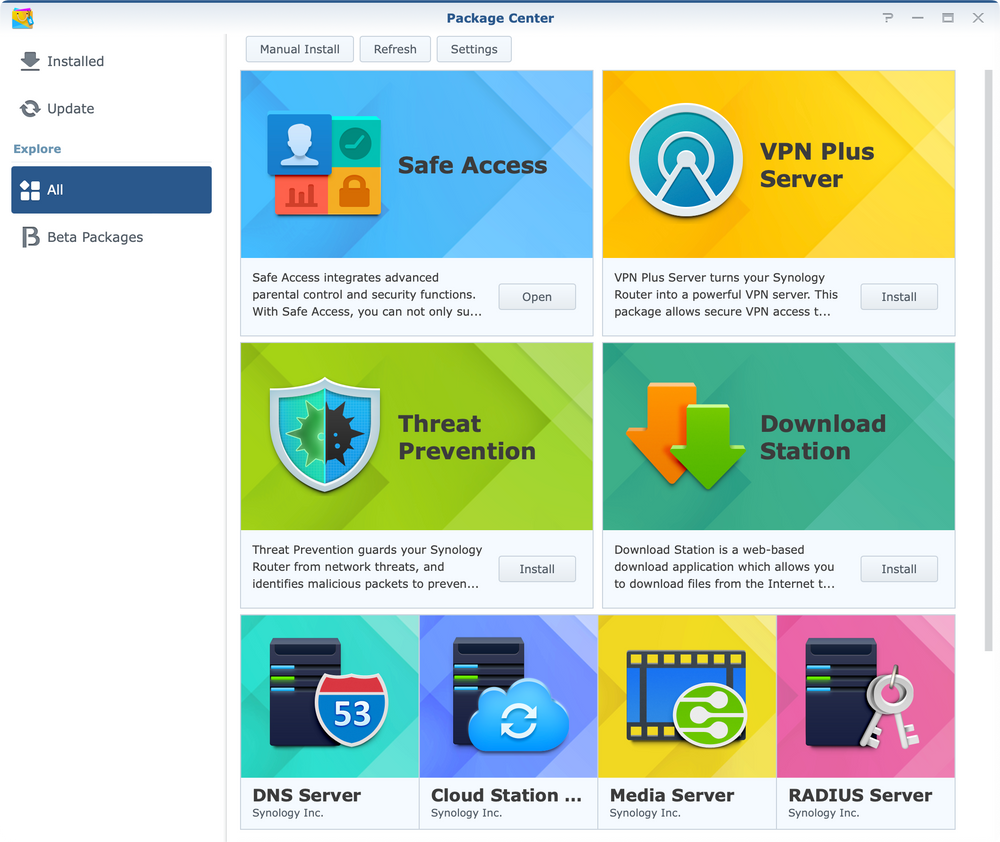
SRM offers the same principle when it comes to the installation of new apps and that would be to install them using the Package Center. There are a total of 8 apps and none are mandatory.
Safe Access as mentioned before is installed by default while others need to be manually initiated if needed.
Most apps will work directly on the router itself, but again, as said before, some will require external storage. Threat Prevention is one, while Download station is another.
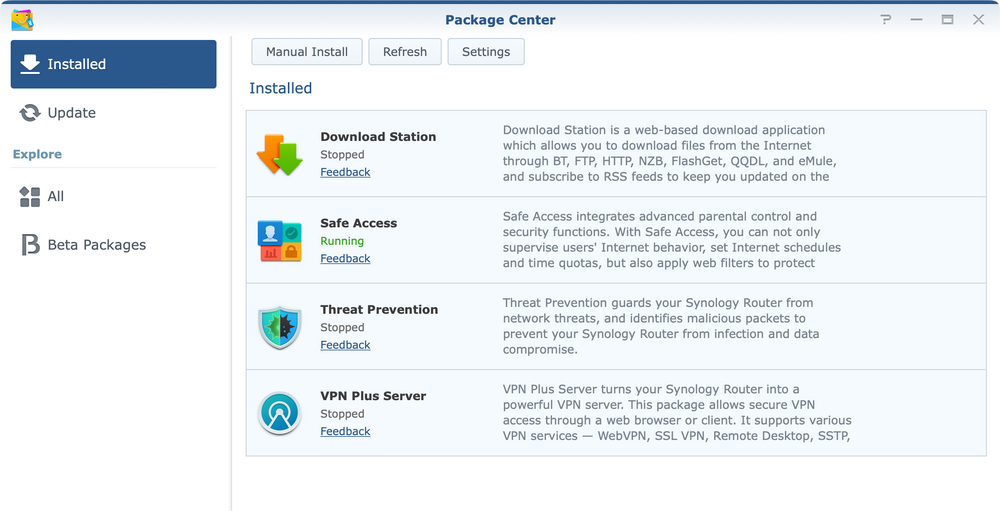
From the listed apps it is clear that the router can be more than a simple web edge device. If needed it can be a simple NAS device with a large enough storage, a VPN server, and even a simple media streaming solution.
How the router will be configured is up to the user, but personally, I would advise using a specified device for any non-router/Internet-related tasks, so as to not burden the router itself and allow it to maximize its resources for its primary operations.
This way it will offer the best possible speed in terms of upload and download transfers as well as perform well when it comes to security layers as well.

: Wi-Fi support and speed test
With my personal limitation and access to Wi-Fi 6 capable devices, this time around I had iPhone 11 and iPhone 13 as test units.
As noted before, this is a Wi-Fi 6 router and as such (identical setup of antennas as RT6600ax) will have similar speeds in terms of usage.
Setting and administrating Wi-Fi networks on your Synology router is done using the Wi-Fi Connect module.
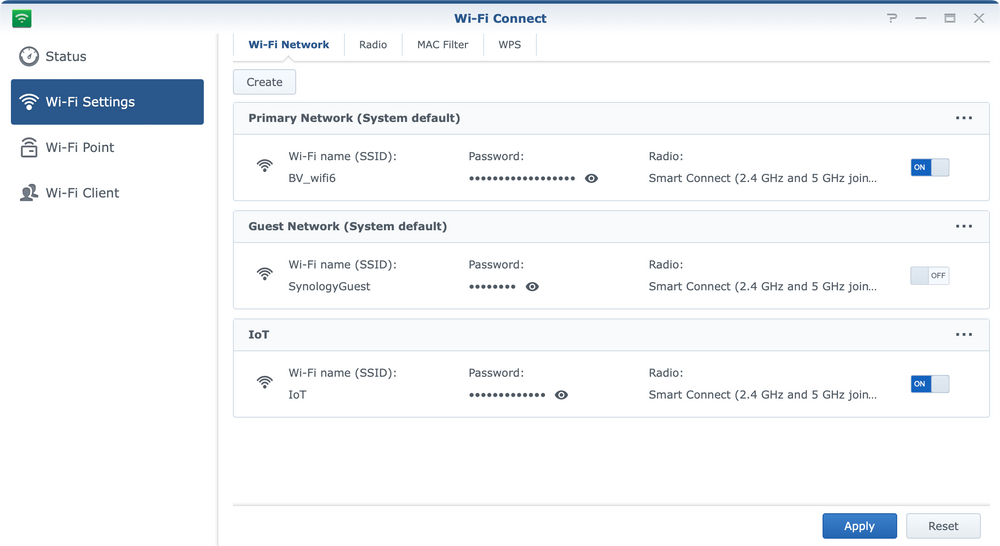
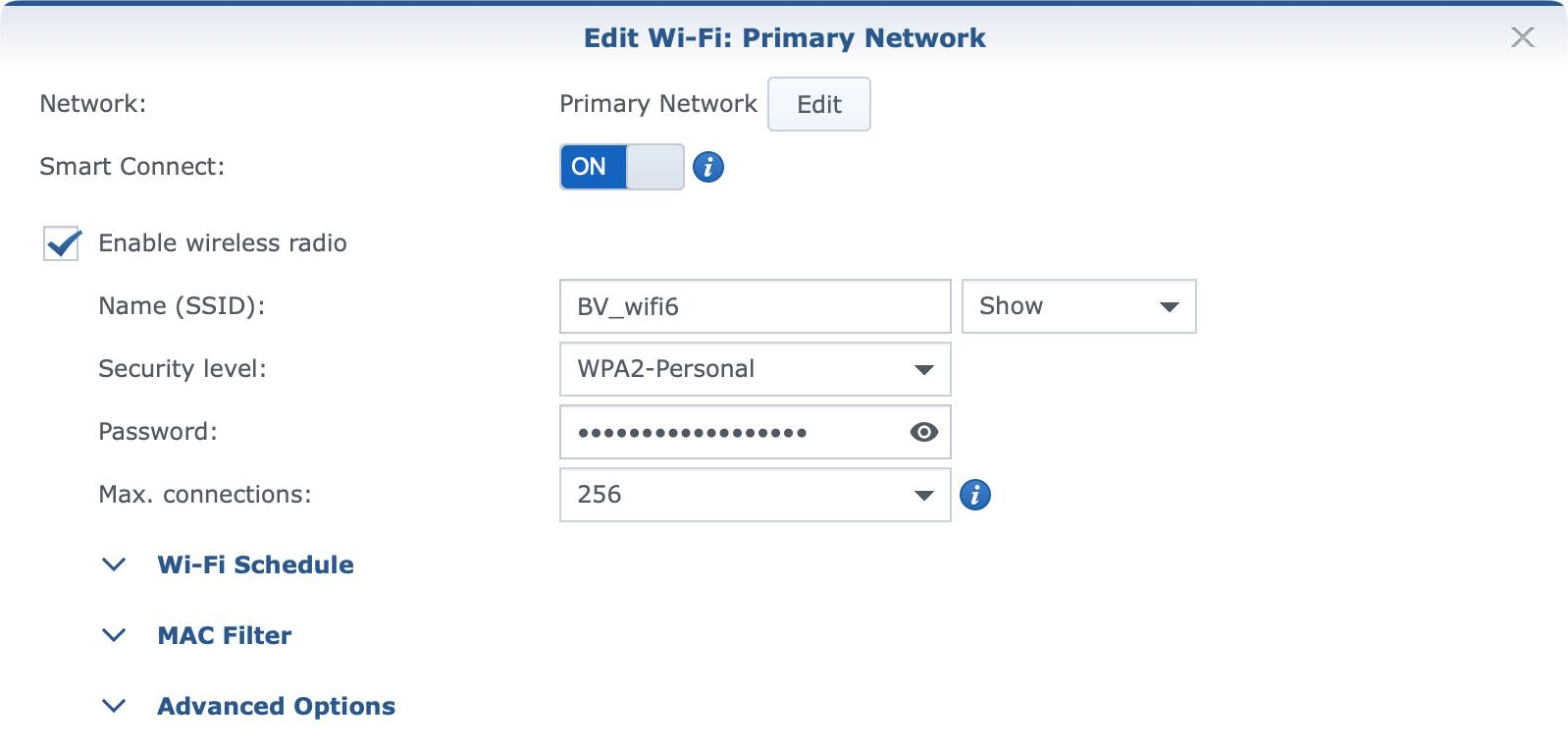
Inside it, you can create, configure and edit your wifi networks in terms of names, radios, passwords, channels, and "smart" controls.
On top of that, each wifi network can now have options for Wi-Fi scheduling, MAC filtering, and a number of other advanced features.
:: Mesh configurations
RT2600ac and MR2200ac routers introduced wifi mesh features in SRM back in the day. The same options are present now with WRX560 and RT6600ax routers, but be mindful of the combination of mesh configurations (table below).
In case you are not familiar, Synology mesh requires all devices in the mesh to be up-to-date and on the same SRM version. In fact, once you deploy a mesh, you can update it from a central (main) device that will push updates to any other wifi point in your network.
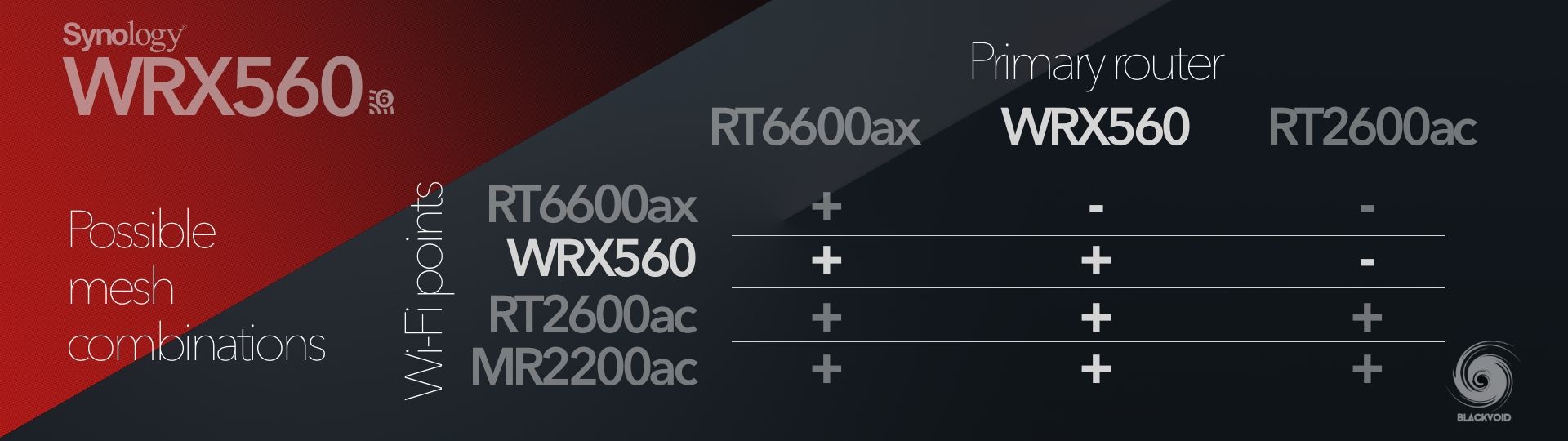
From the table, it is clear that there is a possibility to combine all four current routers but in a certain way. In short, the most powerful device should be the main device in the mesh, meaning that if anyone is running an older model, and also got either the RT6600ax or this WRX560, they will have to reconfigure the network in order to proclaim this device as the "main" one in the mesh.
Not really a move that makes sense to me, especially with the same SRM version prerequisite, but it is what it is. The upside is that older models (non-AX) are able to work with the new devices, so I guess a reconfiguration is the only thing that leaves a bit of that bitter taste.
:: Speed tests
Because the 2.5G WAN speed was still not an option for me to test out (reasons noted at the beginning) all Internet speeds maxed out at 1G without any problem, but of course, it will depend on the actual device and the type of connection (wi-fi vs ethernet).
As pointed out at the start of the section, the test devices will be wi-fi 6 capable (a pair of iPhones) in terms of Internet and wi-fi (LAN) speeds.
On top of those tests, I have done a quick 4G test using a Huawei 4G stick. As expected the Internet speed was not that great but that will heavily depend on a number of factors. The 4G signal was not that great and reflected the speed results.
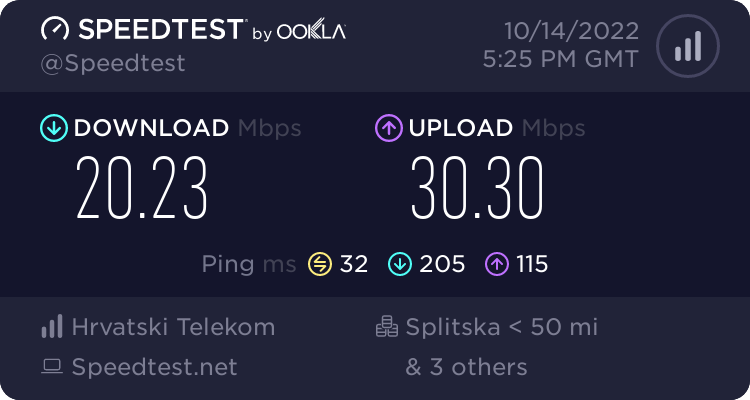
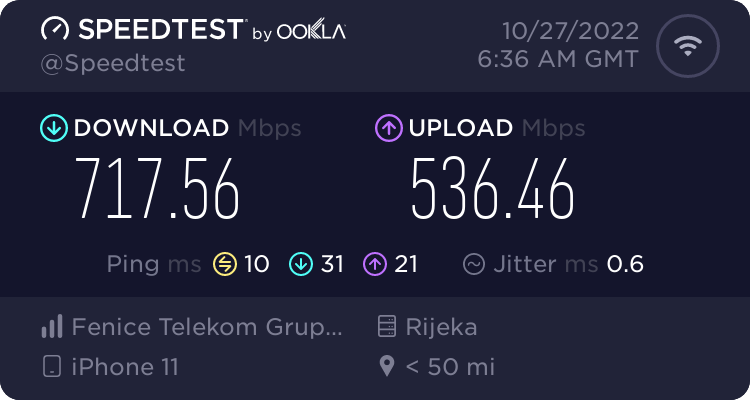
On the other hand, the wi-fi 6 connectivity using a fiber connection via WRX560, gave a different result that also varied depending on the test server in the background as well as the rest of the wi-fi traffic on the device at that time.
In an isolated scenario, with a single device on wi-fi (iPhone 11), the speed tests were consistent and in most cases were north of 700Mbits.
Regarding local wi-fi transfers (via the iPerf3 tool), the speeds were various as well depending on the distance and the generation of the device.
iMac (2017) Wi-Fi AC <> iPhone 11 Wi-Fi 6
In this case, the transfers were in most cases similar and averaged about 290Mbits/s.
Accepted connection from 192.168.1.54, port 57872
[ 5] local 192.168.1.87 port 5201 connected to 192.168.1.54 port 57873
[ ID] Interval Transfer Bandwidth
[ 5] 0.00-1.00 sec 30.4 MBytes 254 Mbits/sec
[ 5] 1.00-2.00 sec 34.8 MBytes 292 Mbits/sec
[ 5] 2.00-3.00 sec 36.7 MBytes 307 Mbits/sec
[ 5] 3.00-4.00 sec 34.2 MBytes 286 Mbits/sec
[ 5] 4.00-5.00 sec 33.0 MBytes 277 Mbits/sec
[ 5] 5.00-6.00 sec 40.2 MBytes 337 Mbits/sec
[ 5] 6.00-7.00 sec 35.3 MBytes 296 Mbits/sec
[ 5] 7.00-8.00 sec 36.3 MBytes 304 Mbits/sec
[ 5] 8.00-9.00 sec 36.2 MBytes 303 Mbits/sec
[ 5] 9.00-10.00 sec 34.8 MBytes 293 Mbits/sec
[ 5] 10.00-10.24 sec 1.82 MBytes 64.8 Mbits/sec
- - - - - - - - - - - - - - - - - - - - - - - - -
[ ID] Interval Transfer Bandwidth
[ 5] 0.00-10.24 sec 0.00 Bytes 0.00 bits/sec sender
[ 5] 0.00-10.24 sec 354 MBytes 290 Mbits/sec receiver
iPhone 13 Wi-Fi 6 <> iPhone 11 Wi-Fi 6
When using two wi-fi 6 capable devices, the speeds are better but nothing groundbreaking. Around 30% better speeds than when using AC Wi-Fi devices with an average of about 420Mbits/s.
Accepted connection from 192.168.1.196, port 49664
[ 7] local 192.168.1.54 port 5201 connected to 192.168.1.196 port 49665
[ ID] Interval Transfer Bitrate
[ 7] 0.00-1.00 sec 42.9 MBytes 360 Mbits/sec
[ 7] 1.00-2.00 sec 49.1 MBytes 412 Mbits/sec
[ 7] 2.00-3.00 sec 50.5 MBytes 423 Mbits/sec
[ 7] 3.00-4.00 sec 51.2 MBytes 429 Mbits/sec
[ 7] 4.00-5.00 sec 51.0 MBytes 428 Mbits/sec
[ 7] 5.00-6.00 sec 49.9 MBytes 418 Mbits/sec
[ 7] 6.00-7.00 sec 52.8 MBytes 443 Mbits/sec
[ 7] 7.00-8.00 sec 49.3 MBytes 414 Mbits/sec
[ 7] 8.00-9.00 sec 51.0 MBytes 427 Mbits/sec
[ 7] 9.00-10.00 sec 51.2 MBytes 430 Mbits/sec
[ 7] 10.00-10.04 sec 1.89 MBytes 402 Mbits/sec
- - - - - - - - - - - - - - - - - -
[ ID] Interval Transfer Bitrate
[ 7] 0.00-10.04 sec 501 MBytes 418 Mbits/sec receiver
With the growing number of wi-fi 6 capable hardware, both WRX560 and RT6600ax will definitely be an excellent future-proof purchase. Backward compatibility with AC and even older wi-fi devices will ensure that even if this model will become part of any environment not populated with wi-fi 6 devices, it will make good use of them.
: Conclusion
So is WRX560 worth getting? With a price of about €209 +tax, if this would be anyone's main device it would still be worth looking at, even with some small SRM hiccups. On the other hand as an extended device in a compatible mesh setup, it would make sense to get the feel of a big and stable network for all wi-fi needs.
Anyone that hasn't used a mesh system before has no idea what they are missing, so if the target environment is big enough it will be more than easy to mesh multiple devices in one large network for that feel of maximum speed and accessibility.
Again, keep in mind that this unit will have to be the main unit in a mesh setup if combined with older models, but on the other hand, it will be a slave unit if meshed with the new RT6600ax.
SRM will continue to evolve for sure and make the network more stable, secure, and future-rich. Investing in a good and quality router will for sure pay off in the end, and WRX560 alone brings a lot to the table for any type of SOHO usage.





