Cybersecurity Awareness Month - October 2022

: Intro
Since 2004, October is Cybersecurity Awareness Month, and this article will cover some of the elements that an individual might implement in order to better protect themselves, their data, and any other sensitive information while using today's devices and technologies.
While we all benefit greatly from the advancement of technology every day, it is important to be aware of potential threats that are present on the Internet in many shapes and forms. While there are whole branches of education and businesses dedicated to cybersecurity, the following text will focus on the end-user options that are available for the SOHO segment, and what Synology as a company has in its portfolio to help in said scenarios.
: Cybersecurity and Synology
Security and protection of digital assets have always been a priority but even more so since a large number of the population are using today's devices and services to improve their quality of life. In return, this means that "our lives" are on those devices, clouds, and servers all across the globe.
While for the most part that is great, as it helps us in a busy and fast-paced rithym of modern living, it is also a huge opportunity for those looking to get the advantage of precious data. Hack attacks, ransomware, data corruptions, and service downtime, are all real and present daily threats that are affecting not just large corporations or banks, but individuals as well.
Synology as a company has been focusing in the past 10y on hardening its security from a software standpoint as well as safeguarding our data on a physical level. The main route that can be achieved was to cut down 3rd party software as much as possible while focusing on their own proprietary OS and applications. Currently, Synology is authorized as a CNA (CVE Numbering Authority) by the MITRE Corporation, a world-leading security institute. This gives them the ability to assign CVE IDs to vulnerabilities affecting their own products, in order to further advance security solutions.

The company has also established Synology PSIRT (Product Security Incident Response Team) responsible for reacting to Synology product security incidents. The PSIRT manages the receipt, investigation, coordination, and public reporting of security vulnerability information regarding Synology products.
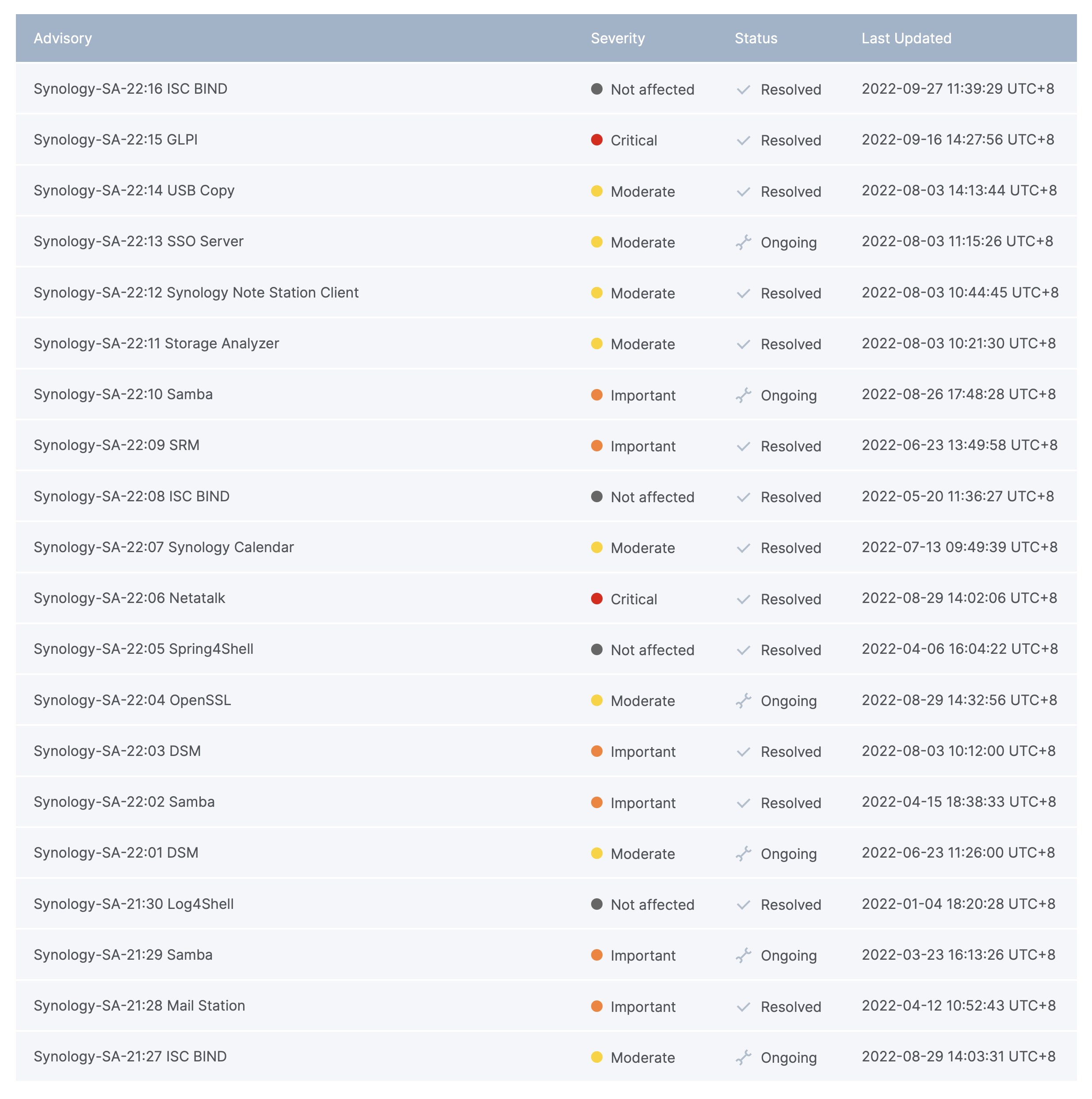
The information listed above can be configured as an email notification using the Synology Account portal, or via an RSS link that can be downloaded via any compatible client.
While Synology is working to safeguard their apps and services as the next company, the main way to protect ourselves is to utilize the tools given to harden our devices as best as possible in order to prevent any incoming threats. In case we do get compromised in any way, there are platforms and apps in the Synology lineup that will help in recovering from such an event should it occur.
: SRM
One of the main ways to protect your home or office from outside threats is your router or edge device. Running with an ISP router will get you out into the wild, but in terms of protection, it will not do much, if anything. If we look at the OS and its options from a standard security standpoint those are poor at best.

Using a custom aftermarket router from any brand will be a much better solution when it comes to security, as well as getting better wifi and WAN speeds, or some other features, like VPN for example. Since 2016, Synology has expanded its offering of products to include routers as well.
While the hardware element is important, the main benefit of running a custom router is its operating system. In the case of Synology routers, that would be the Synology Router Manager (SRM). The latest version 1.3 came with a new flagship model, the RT6600ax, and it offers even more ways to protect your network and assets behind it while offering greater connectivity and speeds across the board.

Applications and configuration options of said OS are the foundation of network security, and SRM has more than a few of them at our disposal.
:: Safe Access, VPN, Threat Prevention, and other security elements of SRM
On the previously linked URL, we can see many of the new and existing features that SRM brings in the new 1.3 version. In terms of security and protection along the already existing firewall, auto block, DDoS protection and IPS/IDS platform, Threat Prevention, SRM also comes preinstalled with Safe Access.
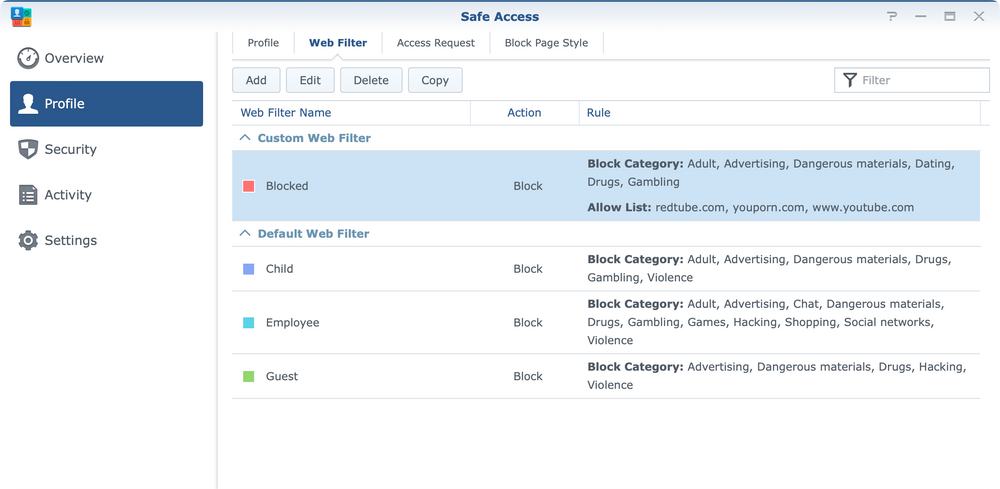
Safe Access offers ways to protect your network, users, and devices from outside threats as well as offers administrators better monitoring, and Internet access schedule setup to limit usage in certain hours or over a certain quota.
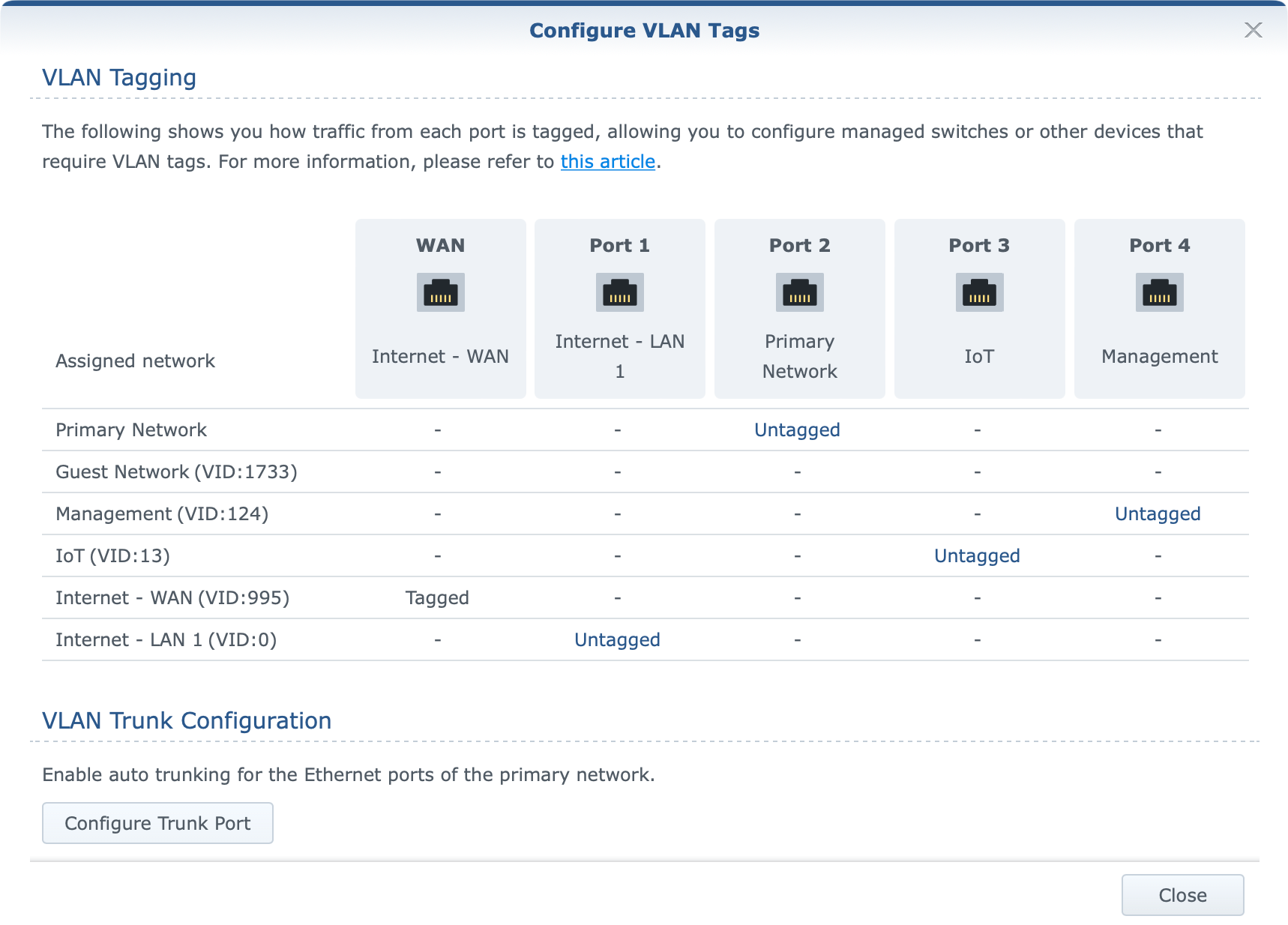
The biggest feature request has managed to find itself in the new SRM version, VLAN support. With this feature users are able to create up to 15 individual networks in order to separate devices from each other or from the Internet completely if necessary. With this separation, both users, and the devices in question can be better protected from any threats, both external and internal.
On top of these SRM features, one frequent usage of managing external access back to your network is via VPN.

Setting up a VPN server will allow for a secure and encrypted private tunnel and access to all the resources as the access is being executed internally, from within the local network. This is one of the safest ways to access any resources that are inside an internal network without exposing them directly to the Internet.
Most popular VPN protocols like IPSec and OpenVPN are supported, but SRM also includes some custom methods of connecting like clientless and over the browser, but it does not offer the new Wireguard protocol (at the moment).
There is a way to utilize Wireguard protocol on a Synology NAS if it's an option by installing support for WG and creating a Docker-driven WG server. More details on this method can be found in the following articles:


In any event, another point that is very important when we talk about routers is port forward. If there is a need for hosting any service or allowing for any incoming traffic towards a machine or a server in the network, opening port(s) will be needed. This will be the easiest way for any outside threat to brute-force your network in order to gain access.
Be extremely careful what and how is forwarded as well do you need it at all. Considering the router is in most cases an edge device, there is a lot that depends on it. Be sure to make it as secure as possible in order to protect the network, devices, and users behind it.
: C2 Password
Another huge problem with identity safety as well as the safety of all virtual accounts for the growing number of online services is account management. Whether it's a bank account, streaming service, forum, or blog, in almost all cases those require some form of login method.
Remembering all various combinations of login accounts and passwords is near impossible, let alone using the same one for all services (do not do that!), so it would be best to invest in a password manager solution or passwordless method if possible (more on this later). While this is nothing new, many still do not use any password/account manager, but rather risk using the same or in the best case several permutations of frequently used passwords in order to mitigate the use of a custom tool.
The best password is the one that a) doesn't have to be entered or b) is very complex and unmemorizable. While there are many password manager solutions out there to date, some free, some commercial, almost all of them will be a much better solution than writing your passwords on a piece of paper "hidden" below your keyboard.

Synology has also recognized this with the deployment of their free password manager as part of their C2 cloud portfolio, C2 Password.
C2 Password offers a number of features that will allow anyone to start with a secure password manager and use it in any situation via the web, desktop, or mobile device.
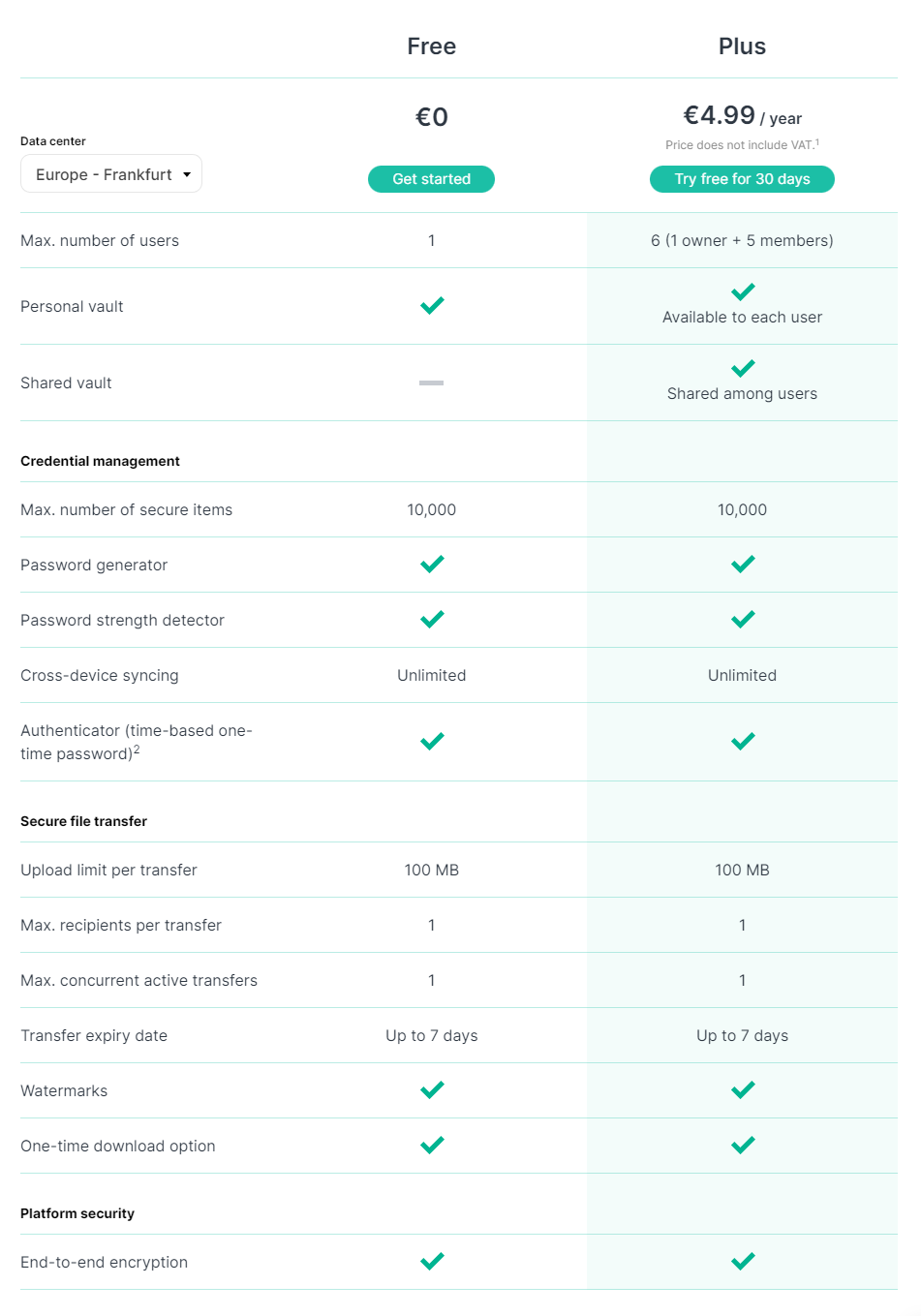
In the event, that hosting confidential and private information on a remote vault is not an option (regardless if it's Synology or 1Password for example), one could also self-host such a platform. Running such a solution on a NAS device is also possible that will keep all data on-premise without giving it away to a cloud provider that is not under your control.
One such solution is Bitwarden that truth be told, also offers a commercial/cloud service. But on top of that, the solution is open source and can be self-hosted as well. For more info on that method, consult the following article and see how to host this solution using the Docker platform on a NAS device.

Regardless if we use one route or the other, it will be better and safer than using the same credentials for multiple identity profiles. The risk is just too high, so consider elevating personal security, without sacrificing too much convenience.
: NAS hardening
While everything said so far can apply to anyone having Internet access, moving inside a home or office network where we might have certain devices like a NAS, is a new layer of features and possibilities, but also another huge area that needs security evaluation and hardening.
A NAS offers a world of options in terms of self-hosted apps and services that we can access from anywhere and virtually from any device. This is all fine and great but just as before, here we also have a very desirable target for malicious attacks, data corruption, and ransomware.
:: Best practices, Secure SignIn (Passwordless)/MFA, Ports, Reverse Proxy
If running a NAS device is something that is being done for the first time, pay close attention if external access is in question. Even if the device will not be exposed, there are still steps needed in order to change the default setting and configurations to avoid easy exploits.

In the listed link above are some of the initial settings that should be considered and taken into account when setting up a new NAS. Be sure to go over it as it describes what and how to change in order to move away from the default DSM configuration.
Building on the previous article there are more advanced elements that were also introduced with the recent major update to the DSM 7 OS. Those are focusing on user access protection as well as passwordless access to the OS itself.
Password manager was also mentioned in this article as one way to make sure not to use the same account and password for any online service, including NAS access. If however, access to the device is of importance, and shouldn't be included in the password manager platform, DSM offers a new passwordless method of authenticating, Secure SignIn.

The passwordless method will allow DSM login using a Synology Secure SignIn mobile app (mobile device and the app are required*) or a compatible hardware key. This way there is no fear of entering your password on a potentially harmful device or OS as the authentification is done on a mobile device. Furthermore, if the device has biometric protection, in order to authenticate, a person first needs to unlock the device using some biometric method before allowing the login process to complete.
If this process is not possible or complicated, DSM offers a more conventional way of utilizing two-factor authentification on top of the username and password of the account. 2FA can be managed with the before-mentioned password manager or any other 3rd party compatible platform for the role.
NAS in itself offers access to any number of services and apps for any number of users, both local and remote. In some cases, the configuration might be needed to allow access to those apps by opening specific ports in the firewall or the router. This is the moment where Internet exposure comes to light. As mentioned before VPN would be the best solution in this case, but if that is not an option, port forward using a public IP address or DDNS could be one solution. Another would be using Synology's QuickConnect method which will allow for a remote connection without the need for port configuration at all.
The point here is that default ports should always be changed, especially if the NAS will be exposed to the public network.
Another way to access any service or app on the NAS without exposing an array of ports and opening potential attack vectors is by using the reverse proxy. With reverse proxy access to internal resources will be possible using a public domain name over a port that is configured (usually that is HTTPS/443) without the need to push multiple ports to the Internet and that way expose the NAS to attacks.

An added benefit of a reverse proxy is that the public name of the service can remain the same (the one accessible to end users) while internally pointing to another port or even host inside the network. This will allow for a more transparent and seamless experience for the user as well as open the possibility of running a highly-available setup for a specific app or service.
DSM has a built-in version of NGIX as its reverse proxy platform, but if users find it somewhat limiting, there is an option to run a custom version inside Docker on NAS models that are compatible to run it.
: Backup & Monitoring
While prevention is the best method of protection, relying on it alone is not a safe way to go. The main reason is that all devices might fail at some point, or there might be an exploit that was not considered or covered so the data still gets compromised. This is why monitoring and backup have a vital role when it comes to cybersecurity and protection.

Synology has a number of tools and platforms when it comes to backup and monitoring. From backing up endpoint devices such as a computer to cloning a complete NAS (including its OS). Also, most of the tools support a number of cloud providers as their backup destination as well as Synology's very own C2.
:: ABB, HB, SR, AI
Due to increased threats from corruption and ransomware, Synology has a few backup tools to help you protect data on devices by backing them up to a NAS. This is also true for accidental deletion as a common user mistake.

Both Active Backup for Business and Synology Drive will help in cases like that, as they offer backup and sync options that can be both used at the same time if that is a particular need.

Active Backup for Business is a new platform in Synology's portfolio and its main task is to provide users with a free option to back up any number of computers, servers, or virtual machines onto the NAS itself.
Windows, Linux (most distributions), and soon macOS are supported as well as the Windows Server platform, and two popular hypervisor platforms (Hyper-V and VMWare ESXi) when it comes to backing up virtual environments.
Following the release of DSM 7, ABB has gotten a new feature as well. One that has been long requested by the users, backing up the NAS and its OS. What this means is that with ABB we can now back up one NAS with its data and OS to another one for any type of worst-case scenario. Also, it will allow for a bare metal recovery on a compatible device.

Everything mentioned so far will be beneficial in case there is ever a need to recover due to some major exploit, data corruption, or hack. On top of this, ransomware is also a very common threat nowadays that can cost a fortune to recover from unless there is no proper backup in place. Even then it will take time and money to get back on track, but at least there is a solution.

Another tool in Synology's arsenal is Snapshot Replication. This tool will allow for the creation of local and remote (on a secondary compatible NAS) snapshots that are in read-only mode, in order to protect against ransomware threats. While not being classified as a backup, local snapshots are the fastest way to recover from corrupted or encrypted data that can also be configured as a remote snapshot (on another device) in case something happens to the original one. An example of disaster recovery in case there is a NAS failure, and how to recover a service running on the NAS can be read in this article.
As mentioned before, monitoring is also a key component when it comes to cybersecurity. Getting notified when there is an issue is very important, and DSM as well as SRM, both offer ways to alert when there is an issue. Synology has also rolled out a semi-free platform for NAS monitoring in terms of hardware, service, backup, and user activity called Active Insight.
As an off-premise monitoring solution hosted by Synology, AI offers ways to get to your metric, logs, and alerts from anywhere at any point in time in order to see what the possible problem might be. As the newest feature addition, AI offers login attempts monitoring and notifications in case there are any abnormal login patterns being detected.
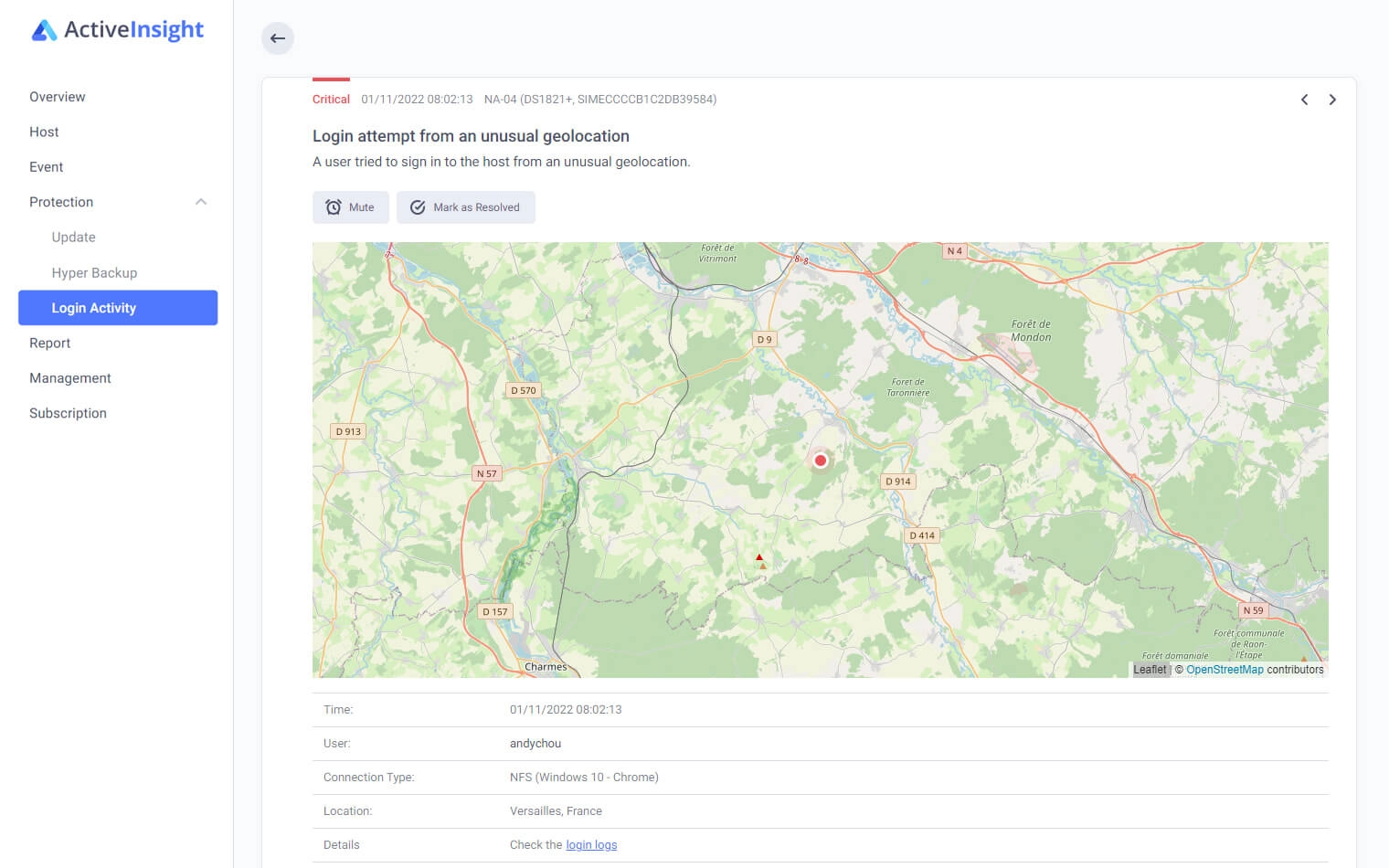
The main benefit of this platform is the fact that it can monitor multiple devices at the same time so a single platform will offer a great overview of all activities happening on any number of NAS devices.
: Updates
Finally, one absolutely important element when it comes to the security of any device or software platform. Updates. Keeping up to date with OS, app, or service updates is crucial. By doing so we are already eliminating a large number of security issues that could be exploited in order for an attacker to gain access and do further damage.
SRM and DSM both need to be patched to the latest update as well as any other application or platform being used on said devices. Also, follow the security advisor page (mentioned at the top) to stay current with any detected, ongoing, and resolved issues.
Patching and updating are sometimes tedious and problematic as it requires testing and downtime, but in the long run, it is worth it compared to the number of potential problems if neglected.
Make sure to check the internal Update and Restore sections or visit the Download Center page for the latest version of OS and app updates.
: Conclusion
Staying safe and secure in today's web of information, online services, and content can be challenging. Security of both home and business elements has reached new heights and education on the matter is mandatory at least to a degree. It is appreciated that Synology works on making complex security features, and platforms accessible to anyone without requiring too much technical knowledge on behalf of the user.
With both DSM 6 and the new version 7, Synology has focused on hardening its services, apps, and hardware to elevate security to a new level. With that, lack of comfort is usually the first thing that we will notice, but both are in a constant balance when it comes to choosing something that works best for us as opposed to how secure it actually is.
It will always be the user's effort and compromise that will determine how much we value our privacy, our data, and overall security. The main thing to remember here is that there is always more you can do when it comes to security and safeguarding your assets and data. However, when, why, and how to implement those elements will always fall on just one thing. You.





